Update
I've found that ForceBindIp in fact is passing parameters to the called executables. It just omits first parameter. So I've modified my script to use ForceBindIp.exe instead of custom injector and now it looks like all issues with injectory exceptions are gone and everything works.
Here is modified steps and BindIp.cmd script:
Install ForceBindIp as usual
Put BindIp.cmd anywhere on your drive (e.g. C:\BindIp\BindIp.cmd)
BindIp.cmd script:
setlocal
:: IP to bind to
set IP=192.168.128.85
:: Common variables
set RegIFEO=HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options%~nx1
set Injector=ForceBindIp.exe
:: ForceBindIp swallows first parameter passed to target exe,
:: so we inject dummy parameter just before it
set AllParams=%*
set FirstParam=%1
call set TargetParams=%%AllParams:*%FirstParam%=%FirstParam% Dummy%%
:: Delete debugger for the target exe in registry,
:: or we'll end in an endless loop of the batch files
reg delete "%RegIFEO%%" /v Debugger /f
:: Start target exe via ForceBindIp
%Injector% %IP% %TargetParams%
:: Restore this script as debugger for the target exe in registry
reg add "%RegIFEO%" /v Debugger /t REG_SZ /d "%~dpnx0" /f
:: Debug, uncomment if needed
rem pause
endlocal
Then follow steps 2-6 from below.
Introduction
ForceBindIp can't automatically inject BindIp.dll to child processes and doesn't pass parameters to the called executables. But I was able to circumvent this by using Image File Execution Options in registry, batch script and third-party dll injector. Details are below.
Theory
To use BindIp.dll without ForceBindIp.exe we need to find out how they communicate (ForceBindIp.exe has to pass IP-address to dll somehow).
I've used IDA free and found that ForceBindIp.exe creates environment variable with name FORCEDIP that holds IP-address and BindIp.dll reads IP-address from this variable when it injected and executed in target process.
To detect target application launch, we can add a Debugger key in the Image File Execution Options in registry for this executable:
Kernel32!CreateProcess when called without the DEBUG_PROCESS or
DEBUG_ONLY_THIS_PROCESS creation flags, checks the registry to see if
IFEO has been set on the executable that it is launching. If yes, then
it simply prepends the debugger path to the executable name,
effectively getting the executable to launch under the debugger.
The "Debugger" in our case, will be a batch script, that will set FORCEDIP variable and launch the injectory dll-injector. Injectory then will start process, pass command-line arguments and inject BindIp.dll.
Practice
- Create folder somewhere (
C:\BindIp for example) and put those three files in it:
BindIp.cmd script:
setlocal
:: IP to bind to. This env.var is used by BindIp.dll
set FORCEDIP=192.168.1.23
:: Common variables
set RegIFEO=HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options%~nx1
set Injector=%~dp0injectory.x86.exe
set BindIpDll=%~dp0BindIp.dll
:: Extract target's parameters, if any
set AllParams=%*
set FirstParam=%1
call set TargetParams=%%AllParams:*%FirstParam% =%%
:: Delete debugger for the target exe in registry,
:: or we'll end in an endless loop of the batch files
reg delete "%RegIFEO%%" /v Debugger /f
:: Start target exe and inject BindIp.dll
if not [%2] == [] (
:: If there were parameters for target exe, pass them on
"%Injector%" --launch %1 --inject "%BindIpDll%" --args "%TargetParams%"
) else (
:: No parameters were specified
"%Injector%" --launch %1 --inject "%BindIpDll%"
)
:: Restore this script as debugger for the target exe in registry
reg add "%RegIFEO%" /v Debugger /t REG_SZ /d "%~dpnx0" /f
:: Debug, uncomment if needed
rem pause
endlocal
- Create registry key (e.g.
LolClient.exe) for target executable in HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\
- Add String Value to this key:
- Name:
Debugger
- Value:
C:\BindIp\BindIp.cmd
Grant Users Full permissions on this key (the script will have to modify it at every launch). It should look like this: 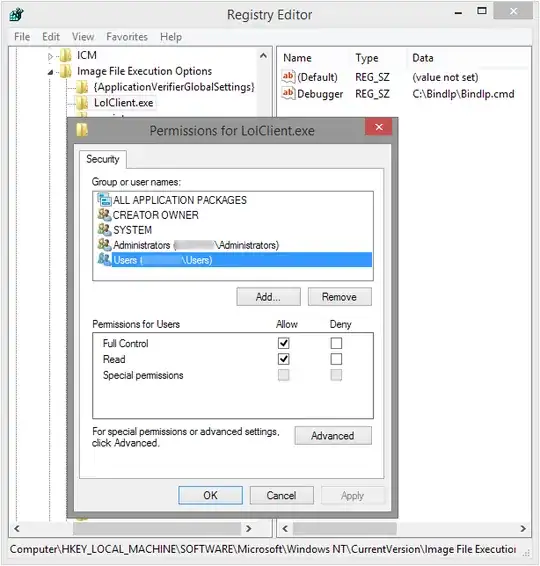
Set required IP-address in BindIp.cmd
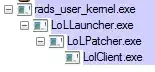
Repeat steps 3 and 4 for every executable you wish to bind (rad_user_kernel.exe, LolLauncher.exe, LolPatcher.exe, etc.).
Now, every time when you launch executable that has corresponding registry entry, the BindIp.cmd script will launch instead and bind this program to desired IP-address.
Conclusion
I've tested this on my laptop running Windows 8.1 x64 and was able to successfully bind various programs (AIMP 2, BersIRC, Opera 12.4) to Ethernet or WiFi adapter using this technique. Unfortunately BindIp.dll is 32-bit, so it wouldn't work with 64-bit processes.