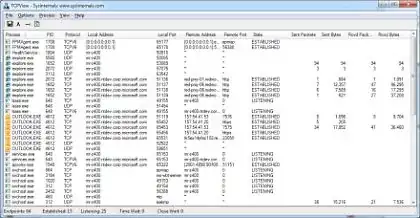
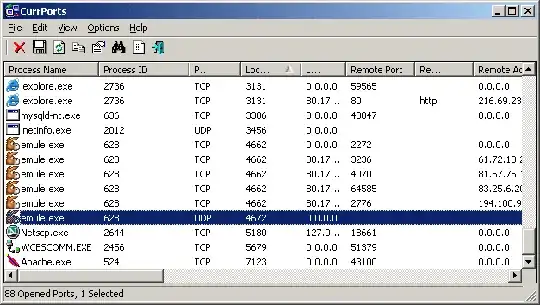
I'm redoing my firewall configuration with more restrictive policies and I would like to determine the provenance (and/or destination) of some outgoing connections.
I have an issue because they come from svchost.exe and go to web content/application delivery providers - or similar:
5 IP in range: 82.96.58.0 - 82.96.58.255 --> Akamai Technologies akamaitechnologies.com
3 IP in range: 93.150.110.0 - 93.158.111.255 --> Akamai Technologies akamaitechnologies.com
2 IP in range: 87.248.194.0 - 87.248.223.255 --> LLNW Europe 2 llnw.net
205.234.175.175 --> CacheNetworks, Inc. cachefly.net
188.121.36.239 --> Go Daddy Netherlands B.V. secureserver.net
So is it possible to know which service does a particular connection? Or what's your recommendation about the rules applied to these ones?
(Comodo Firewall & Windows 7)
Update:
netstat -ano & tasklist /svc help me a little but they are many services in one svchost.exe so it's still an issue. moreover the service names returned by "tasklist /svc" are not easy readable.
(All the connections are HTTP (port 80) but I don't think it's relevant)