Here is a more complete answer based on Justin's:
(Using gpg 1.4.16 on Ubuntu 14)
- Get the ID of your key like this:
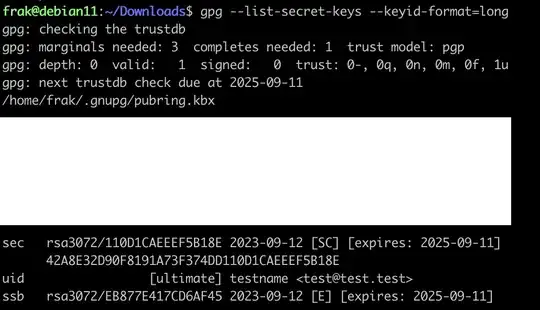
gpg --list-secret-keys --keyid-format=long
This will output a few lines similar to below. The key ID is the value XXXX
/home/username/.gnupg/secring.gpg
----------------------------------
sec 4096R/XXXX <creation date>
uid name <email.address>
ssb 4096R/YYYY <creation date>
Open the gpg key edit submenu like this:
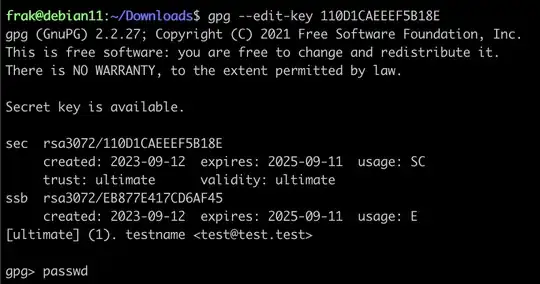
gpg --edit-key XXXX
You will see information about the key.
Type passwd at the prompt to change the password:
gpg> passwd
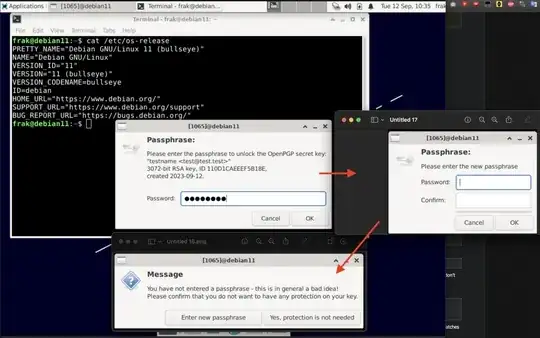
Enter your existing passphrase.
Enter the new passphrase for this secret key. (Leave this blank and press Enter)
Press Enter twice and consider the warnings from the tool and its implications before proceeding.
You don't want a passphrase - this is probably a *bad* idea!
Do you really want to do this? (y/N) y
Similarly On Debian 11: