I have successfully used my YubiKey to get my Chrome and Firefox browsers to get my 2-step verification to work with my Google account.
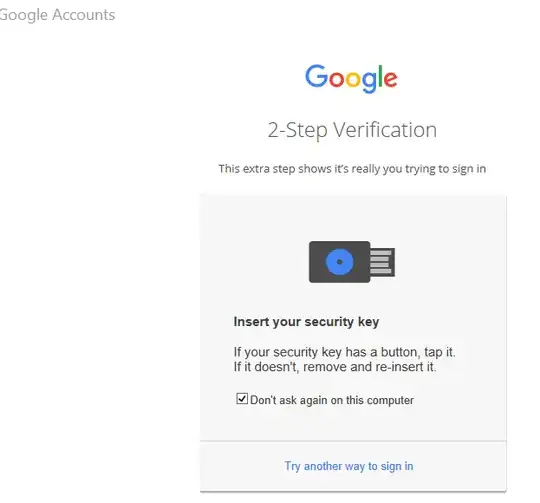
Unfortunately, I have a few Windows applications which I cannot get to work with my key. I enter in my user name in screen 1, password in screen 2, and then I get third the key step:
I am never able to get this window to recognize my key. I can't even figure out what browser is being used for this authentication. My understanding is that Windows' Internet Explorer 11 does not support FIDO or U2F, so I tried disabling Windows Internet Explorer in hopes it would switch the back end to Edge which might work better. It did not.
What can I do to get these applications and others with a similar interface and prompt to recognize my key? If that is not possible, why? Further, if it is not possible, short of leaving 2-step verification, what alternatives are available?
The Windows Mail Application is an example of such an application (this gives a message saying "You can only use your security keys with Google Chrome." Another example of such an application is UpSafe's Free Gmail Backup which takes me to the U2F prompt screen image above.
One of my devices is a Feitian MultiPass FIDO. The other is a Yubico U2F FIDO USB key.