This question is specifically related to the ICMPv4 Timestamp Request (Type 13) message.
When I have Windows Firewall disabled I can send a Timestamp Request from the host and the client will receive the request and respond with Timestamp Reply (Type 14).
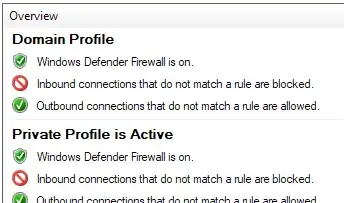
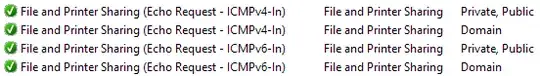
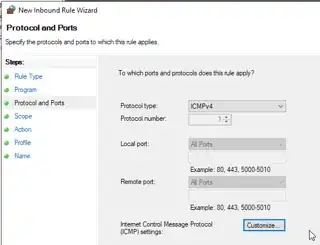
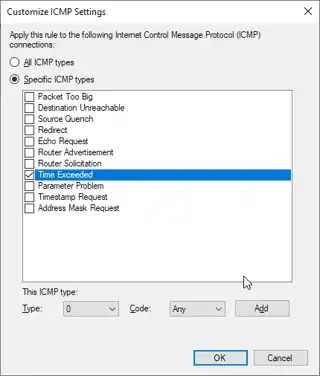
When I have Windows Firewall enabled I can send a Timestamp Request from the host and the client will receive the request but never responds with Timestamp Reply. I'm assuming this is because the firewall is blocking the request. However, I don't see any particular rules setup which indicate to me that this is really the case. Neither could I find any documentation online to help me understand if this particular message is being blocked by default (like ICMP Echo).
Does anyone know if Windows Firewall blocks this message by default? Is there somewhere I can look to see/configure this default setting? Is there documentation available somewhere that I simply missed?
I am using Nping to send the message and Wireshark to watch the packets come and go.
 " link in Control Panel), you see this screen:
" link in Control Panel), you see this screen: