It's possible to download programs called "ransomware decryptors" that are able to, in some cases, completely remove the encryption from ransomware-encrypted files, without the need to pay the attacker's ransom.
There is no point attempting to decrypt your files on a system that may still have an active infection that could immediately re-encrypt them. Start by running Malwarebytes on the infected computer and try to remove the original infection before doing anything else. Leave the 1 TB drive connected to the computer and allow Malwarebytes to scan that also.
Attempt to identify the strain of ransomware using the Emsisoft ransomware identification page and then use the tool they recommend for your particular encryption, if one exists:
You may want to try the six offerings on the Kaspersky No Ransom site, each of which work for multiple variants of ransomware:
- Rakhni Decryptor
- Rannoh Decryptor
- Shade Decryptor
- CoinVault Decryptor
- Wildfire Decryptor
- Xorist Decryptor
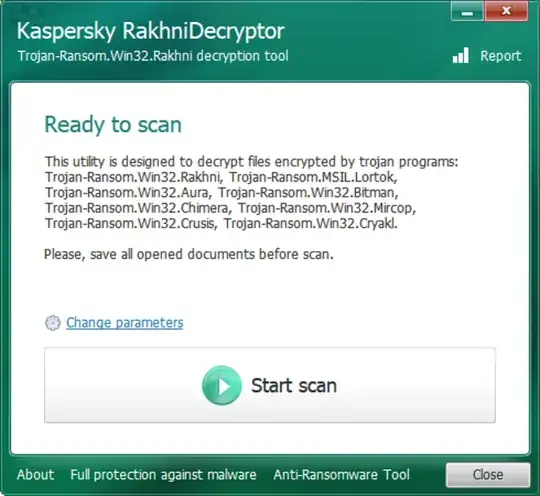
This is what the Kaspersky decryption tools look like in action:
- No More Ransom! has a massive collection of over 100 free ransomware removal tools. Once you obtain the official ID of your ransomware from Step 2, you may be able to find a matching decryptor for it from that list.
Even if none of the ransomware decryptors currently available are able to unlock your files, the ransomware that compromised your system could be defeated later on. I would advise against deleting any of your encrypted files, even if you can't decrypt them today, as a ransomware decryptor that does work for them may become available in the future.
All hope is not lost!

