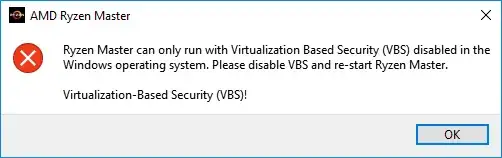
here's how i disabled VBS and LSAISO (the isolated lsa + secure system processes that appear in task manager)
basically this allows you to keep hyper-v installed and working.
no need to uninstall hyper-v or set hypervisorlaunchtype to off
or do the bootmgr device guard / vbs bypass at every reboot...
tl;dr
disable secureboot and also tpm is you want.
(secureboot is a tad annoying anyway as it prevents you from altering the bcd via bcdedit as it says access denied)
just remember to add a bypass to your windows installation media or re-enable these things when doing a upgrade and then turn them off again.
apply the below registry script. (some entries are probably redundant)
but it's more of a try it all just to be sure.
EnableVirtualizationBasedSecurity = 2 disables vbs, i know...why doesn't 0 do it ? not sure.
i posted the following on mdl forums;
first part of post not important...so left out.
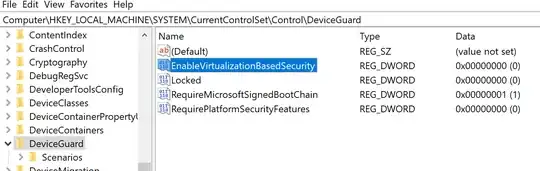
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard]
"Unlocked"=dword:00000001
"Locked"=dword:00000000
"RequirePlatformSecurityFeatures"=dword:00000001
"LsaCfgFlags"=dword:00000000
"EnableVirtualizationBasedSecurity"=dword:00000002
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Capabilities]
"CG_Capable"=dword:00000000
"DG_Capable"=dword:00000000
"HVCI_Capable"=dword:00000000
"OSSKU"=dword:00000000
"SecureBoot"=dword:00000000
"Virtualization"=dword:00000000
"TPM"=dword:00000000
"SecureMOR"=dword:00000000
"UEFINX"=dword:00000000
"SMMProtections"=dword:00000000
"HyperVEnabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\CredentialGuard]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\KernelShadowStacks]
"Enabled"=dword:00000000
some may not be required but i've basically been trying anything and everything.
webpages i used for info;
https://learn.microsoft.com/en-us/a...le-virtualization-based-security-without-disa
https://admx.help/?Category=Windows...dows.DeviceGuard::VirtualizationBasedSecurity
https://learn.microsoft.com/en-us/w...ualization-based-protection-of-code-integrity
https://learn.microsoft.com/en-us/w...ection/credential-guard/configure?tabs=intune
https://learn.microsoft.com/en-us/v...ndows/user-guide/enable-nested-virtualization
https://learn.microsoft.com/en-us/virtualization/hyper-v-on-windows/tlfs/vsm
https://gist.github.com/benhar-dev/1403b4e070655787c3f8ff1e15b1ab73
i think what finally did it was "EnableVirtualizationBasedSecurity"=dword:00000002 which seems undocumented as i found nothing on duckduckgo other than the same entry with values of 0 which is supposed to mean disabled so the group policy stuff says and 1 which is enabled.
it was the last change i made to the registry before it suddenly got turned off.
hyper-v still works and thus no package removals are required or the boot sequence opt out.
i also added vsmlaunchtype Off to bcd also isolatedcontext to No. these are both related to hyper-v but i don't really know if they helped disabled vbs. i know the the vsm one is related to virtual secure machine.
i also disabled secure boot and tpm.
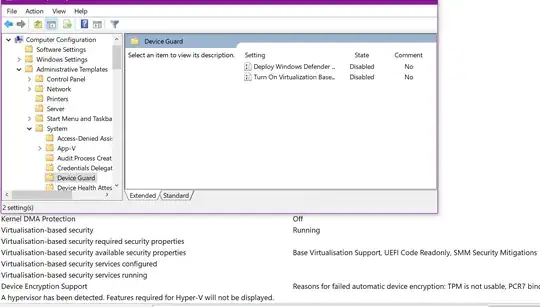
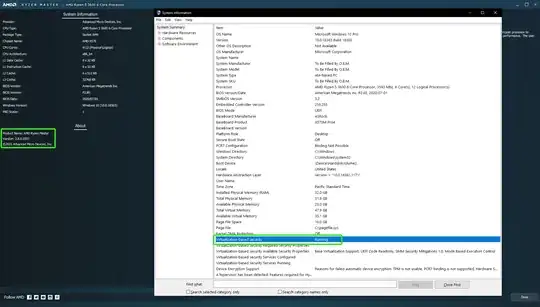
here is msinfo32 output...see attachment.
had to enable nested virtualization to the vm so hyper-v in hyper-v could be tested.
i had to reduce the memory as only 4gb was available and it errored which almost made me think hyper-v was now broken but setting ram to 2gb allowed the vm to power up and work as normal.
so i think i can now pat myself on the back...i think.
edit,
"EnableVirtualizationBasedSecurity"=dword:00000002 = not enabled
(fully disabled and lsaiso is disabled too)
(only if secureboot is disabled otherwise shows as running)
"EnableVirtualizationBasedSecurity"=dword:00000001 = Enabled but not running (only if secureboot is disabled otherwise shows as running)
"EnableVirtualizationBasedSecurity"=dword:00000000 = Running
(only if secureboot is disabled otherwise shows as running)
"RequirePlatformSecurityFeatures"=dword:00000001 = only secureboot as requirement
disabling secureboot results in EnableVirtualizationBasedSecurity setting working on 0,1,2
with securboot enabled, the settings 0, 1, 2 are ignored. only with it off is the user allowed to toggle between 0, 1, 2.
hope that made sense.