Is it possible to access third-party HTTPS pages over an SSH tunnel?
I have to access third-party websites with tight security rules from home-office.
Due to the security rules, only access from my work-PC will be allowed. I can access the work-PC by connecting to the work network through a VPN, and then can access everything via SSH. So I can access the third-party website through a remote wget (useless for a webapp), or by running a browser throw X-forwarding – with terrible performance, making it viable, but painful, for getting work done.
Since the configuration of the VPN cannot be changed due to limitations of the product in use, I have tried to tunnel the traffic to the third party website through the work PC using
ssh MyUserName@MyWorkPC.MyEmployer.com -L localhost:443:ThatCompany.com:443 -N
# | || || | | |
# '.''----.---''--------.------------' '.'
# Port forwarding -' | | |
# | | |
# Allow access to :443 only from localhost --' | |
# | |
# localhost:443 will access ThatCompany.com:443 -----------' |
# through the work PC Don't display shell
# of work PC
If I then try to access https://SubDomain.ThatCompany.com, I will get a 404 code and a page saying
You have reached the webserver of ThatComapany.
The URL you used is unknown to us, so we cannot allow you in.
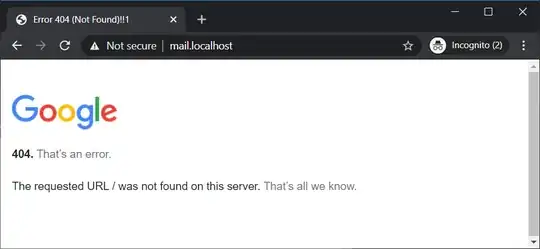
Example: Trying to access Gmail through the tunnel.
The command would be
ssh MyUserName@MyWorkPC.MyEmployer.com -L localhost:443:google.com:443
If I then try to access https://mail.localhost I will get:
This demonstrates two issues:
- The connection isn't considered secure, because the host name doesn't match the certificate.
- The webserver will reject the connection; It probably suspects a man-in-the-middle attack.
Is there some way to configure the forwarding in such a manner, that the webserver won't know about it?