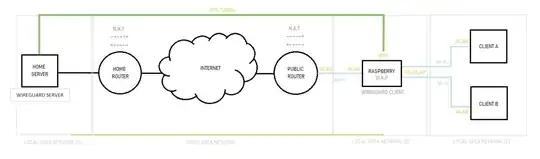
I used to have a simple setup with two raspberry pi's, where the one in my house acts as a wireguard client with a wireless AP and forwards all traffic via a VPN to exit at the remote pi, like this (except in this diagram the server is called home server, while in my setup, the server is remote and the client is local).
 Now I've moved and upgraded my home wifi to two Omada EAP225s wired to a level 2 managed switch from HP. Is there any way to have the remote VPN network served via the EAP225s, rather than through the raspberry pi's wifi AP?
Now I've moved and upgraded my home wifi to two Omada EAP225s wired to a level 2 managed switch from HP. Is there any way to have the remote VPN network served via the EAP225s, rather than through the raspberry pi's wifi AP?
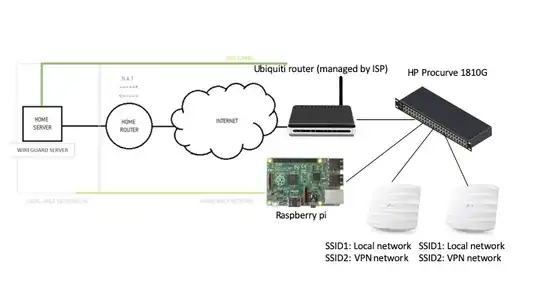
Here's what I have so far:
I set up a vlan on my switch with the ports for the raspberry pi and two APs
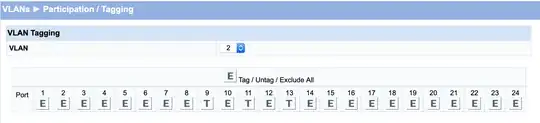 On the raspberry pi I set up a vlan interface with
On the raspberry pi I set up a vlan interface with
sudo nano /etc/network/interfaces.d/vlans
auto eth0.2
iface eth0.2 inet manual
vlan-raw-device eth0
nano /etc/dhcpcd.conf
interface eth0
static ip_address=192.168.1.104/24
static routers=192.168.1.1
static domain_name_servers=8.8.8.8 8.8.4.4 1.1.1.1
interface eth0.2
static ip_address=10.0.0.1/24
static domain_name_servers=8.8.8.8 8.8.4.4 1.1.1.1
I then got wireguard up on wg0 following https://github.com/adrianmihalko/raspberrypiwireguard
This works to establish the connection to the server and curl https://ipinfo.io/ip gives me the public IP of the server
To provide access to connected hosts I set up dnsmasq with sudo apt-get install dnsmasq, then sudo nano /etc/dnsmasq.conf
interface=eth0.2
dhcp-range=10.0.0.50,10.0.0.150,12h
server=1.1.1.1
server=8.8.8.8
server=8.8.4.4
In the EAP controller web interface I set up a new SSID with the following settings

I can now connect to the network with my laptop, and connect to the raspberry pi by ssh, but no web traffic is getting across. What am I missing?