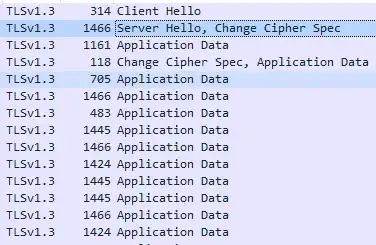
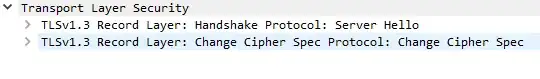
I'm looking at a TLS v1.3 headers in Wireshark and I'm not sure where I would find the server certificate that is used to confirm that the server is who they claim to be.
The Client Sends Hello then the Server Sends Hello with two TLS Record Layers and also sends another Application Data.
but none of these contains anything about a certificate. The client sends back a Change Cipher Spec. and after only Application Data is transmitted which is now obviously encrypted.
Where are the Server's Certificate and Digital Signature as suggested by Mike Pound from this Computerphile video https://www.youtube.com/watch?v=86cQJ0MMses. where is Server Hello Done suggested in the video.
EDIT:
I can see the certificate in TLS v1.2 but not in TLS v1.3