For security reasons I want to sandbox my browser and so I came up with the following wrapper script to run Firefox inside a bwrap sandbox:
$ cat ~/.local/bin/firefox
#!/bin/sh
MYDISPLAY="${DISPLAY##*:}"
MYDISPLAY="${MYDISPLAY%%.*}"
/usr/bin/bwrap \
--unshare-all \
--tmpfs /tmp \
--bind ${HOME}/.cache/mozilla ${HOME}/.cache/mozilla \
--bind ${HOME}/.mozilla ${HOME}/.mozilla \
--bind ${HOME}/Downloads ${HOME}/Downloads \
--bind /tmp/.X11-unix/X${MYDISPLAY} /tmp/.X11-unix/X${MYDISPLAY} \
--ro-bind ${HOME}/.config/mimeapps.list ${HOME}/.config/mimeapps.list \
--ro-bind ${HOME}/.local/share/fonts ${HOME}/.local/share/fonts \
--ro-bind ${HOME}/.local/share/mime ${HOME}/.local/share/mime \
--ro-bind /usr/bin /usr/bin \
--ro-bind /usr/lib /usr/lib \
--ro-bind /usr/lib64 /usr/lib64 \
--ro-bind /usr/share /usr/share \
--ro-bind /etc/alternatives /etc/alternatives \
--ro-bind /etc/fonts /etc/fonts \
--ro-bind /etc/resolv.conf /etc/resolv.conf \
--ro-bind /etc/ssl /etc/ssl \
--ro-bind /etc/ca-certificates /etc/ca-certificates \
--ro-bind ${XDG_RUNTIME_DIR}/pulse ${XDG_RUNTIME_DIR}/pulse \
--symlink usr/bin /bin \
--symlink usr/lib /lib \
--symlink usr/lib64 /lib64 \
--dev /dev \
--dev-bind /dev/dri /dev/dri \
--proc /proc \
--setenv HOME ${HOME} \
--hostname RESTRICTED \
--share-net \
--die-with-parent \
--new-session \
-- \
/usr/bin/firefox "${@}"
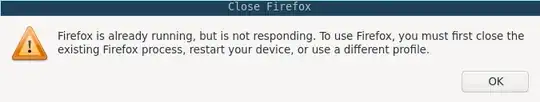
This works pretty well. However, if Firefox is already running and I call e.g. $ firefox "https://example.com" I get the following error:
It is clear to me why this happens: bwrap creates a second sandbox and tries to start Firefox a second time inside the new sandbox.
What I want to achieve: Add a tab to the already running Firefox inside the first sandbox.
Therefore I would have to run the $ firefox "https://example.com" command somehow inside the already existing sandbox. Is there a way to achieve this?