I'm attempting to install a Windows 10 VM using QEMU/KVM in virt-manager. I want to use it for a WinApps setup to do some experiments with Adobe CC in Linux.
I've been following several guides including the Winapps guide on their Github page and this medium article.
The setup is using VirtIO drivers, so I setup the proper CDROM devices with the virtIO drivers, as well as the NIC device, I loaded them at install time, I installed the rest of the drivers on the VM using the VirtIO 64-bit installer in the E: drive of the VM and everything seems to be working except for network connectivity.
I did some digging, network issues with VirtIO seem to have been very common over the years, but the issues I'm seeing don't appear to be particularly common.
The device itself in the Windows Appears to be working, there's no warning icon on it, attempting to update the driver simply tells me that the best possible driver is installed. The devices and drivers work... just no internet.
My system is Pop_OS 21.10, kernel version 5.16.11-76051611-generic.
I would assume there's more setup to do with iptables and configuring ports, but none of those solutions have worked so far.
EDIT: Of course, if there is more info needed to debug this issue, I'm ready to add it, I just don't know what yet.
ADDENDUM 1: For the networking I have not made any explicit setup other than specifying the NIC virtual device to use virtIO. The virtual connection is the default NAT virtual network, which has created a virtual device listed as virbr0 in the ifconfig. No network bridging has been done so far, I've setup about as default as you can go.
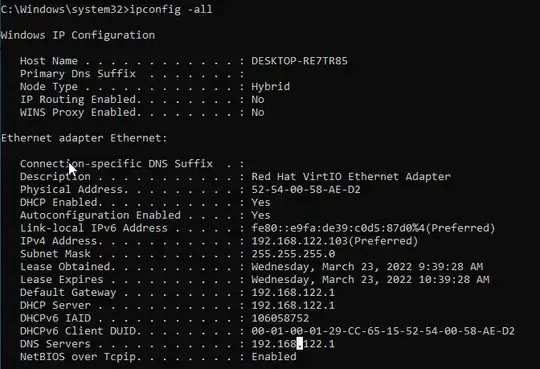
Also on the guest machine, all I have is just the automatically configured local IP and that's it. No access to the host machine or router, at least as far as I'm able to read it. Here's a screenshot:
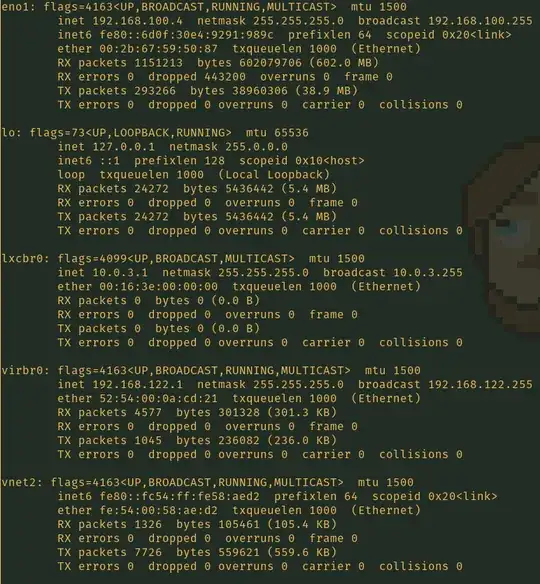
ADDENDUM 2: Here's a screenshot of the host ifconfig:
The eno1 is my main network device, in this case connected via Ethernet. virbr0 is configured to 192.168.122.1
The output of iptables-save is as follows:
# Generated by iptables-save v1.8.7 on Wed Mar 23 14:11:01 2022
*mangle
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:C170 - [0:0]
:C171 - [0:0]
:LIBVIRT_PRT - [0:0]
-A INPUT -j C171
-A OUTPUT -j C170
-A POSTROUTING -j LIBVIRT_PRT
-A POSTROUTING -o lxcbr0 -p udp -m udp --dport 68 -j CHECKSUM --checksum-fill
-A C170 -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff
-A C170 -m mark --mark 0x0 -j NFQUEUE --queue-num 17040 --queue-bypass
-A C171 -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff
-A C171 -m mark --mark 0x0 -j NFQUEUE --queue-num 17140 --queue-bypass
-A LIBVIRT_PRT -o virbr0 -p udp -m udp --dport 68 -j CHECKSUM --checksum-fill
COMMIT
# Completed on Wed Mar 23 14:11:01 2022
# Generated by iptables-save v1.8.7 on Wed Mar 23 14:11:01 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:C17 - [0:0]
:LIBVIRT_FWI - [0:0]
:LIBVIRT_FWO - [0:0]
:LIBVIRT_FWX - [0:0]
:LIBVIRT_INP - [0:0]
:LIBVIRT_OUT - [0:0]
-A INPUT -j LIBVIRT_INP
-A INPUT -i lxcbr0 -p tcp -m tcp --dport 53 -j ACCEPT
-A INPUT -i lxcbr0 -p udp -m udp --dport 53 -j ACCEPT
-A INPUT -i lxcbr0 -p tcp -m tcp --dport 67 -j ACCEPT
-A INPUT -i lxcbr0 -p udp -m udp --dport 67 -j ACCEPT
-A INPUT -j C17
-A FORWARD -d 192.168.122.103/32 -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -j LIBVIRT_FWX
-A FORWARD -j LIBVIRT_FWI
-A FORWARD -j LIBVIRT_FWO
-A FORWARD -o lxcbr0 -j ACCEPT
-A FORWARD -i lxcbr0 -j ACCEPT
-A OUTPUT -j LIBVIRT_OUT
-A OUTPUT -j C17
-A C17 -m mark --mark 0x0 -j DROP
-A C17 -m mark --mark 0x6a4 -j RETURN
-A C17 -p icmp -m mark --mark 0x6a5 -j RETURN
-A C17 -m mark --mark 0x6a5 -j REJECT --reject-with icmp-host-prohibited
-A C17 -m mark --mark 0x6a6 -j DROP
-A C17 -j CONNMARK --save-mark --nfmask 0xffffffff --ctmask 0xffffffff
-A C17 -m mark --mark 0x6ae -j RETURN
-A C17 -p icmp -m mark --mark 0x6af -j RETURN
-A C17 -m mark --mark 0x6af -j REJECT --reject-with icmp-host-prohibited
-A C17 -m mark --mark 0x6b0 -j DROP
-A C17 -m mark --mark 0x6b5 -j RETURN
-A LIBVIRT_FWI -d 192.168.122.0/24 -o virbr0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A LIBVIRT_FWI -o virbr0 -j REJECT --reject-with icmp-port-unreachable
-A LIBVIRT_FWO -s 192.168.122.0/24 -i virbr0 -j ACCEPT
-A LIBVIRT_FWO -i virbr0 -j REJECT --reject-with icmp-port-unreachable
-A LIBVIRT_FWX -i virbr0 -o virbr0 -j ACCEPT
-A LIBVIRT_INP -i virbr0 -p udp -m udp --dport 53 -j ACCEPT
-A LIBVIRT_INP -i virbr0 -p tcp -m tcp --dport 53 -j ACCEPT
-A LIBVIRT_INP -i virbr0 -p udp -m udp --dport 67 -j ACCEPT
-A LIBVIRT_INP -i virbr0 -p tcp -m tcp --dport 67 -j ACCEPT
-A LIBVIRT_OUT -o virbr0 -p udp -m udp --dport 53 -j ACCEPT
-A LIBVIRT_OUT -o virbr0 -p tcp -m tcp --dport 53 -j ACCEPT
-A LIBVIRT_OUT -o virbr0 -p udp -m udp --dport 68 -j ACCEPT
-A LIBVIRT_OUT -o virbr0 -p tcp -m tcp --dport 68 -j ACCEPT
COMMIT
# Completed on Wed Mar 23 14:11:01 2022
# Generated by iptables-save v1.8.7 on Wed Mar 23 14:11:01 2022
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:LIBVIRT_PRT - [0:0]
-A PREROUTING -d 192.168.100.4/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.122.103:80
-A PREROUTING -d 192.168.100.4/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.122.3:80
-A PREROUTING -d 192.168.100.4/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.122.2:80
-A PREROUTING -d 192.168.100.4/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.122.1:80
-A PREROUTING -d 192.168.100.4/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.122.0:80
-A OUTPUT -p udp -m mark --mark 0x6b5 -j DNAT --to-destination 127.0.0.17:717
-A OUTPUT -p tcp -m mark --mark 0x6b5 -j DNAT --to-destination 127.0.0.17:717
-A OUTPUT -p udp -m mark --mark 0x707 -j DNAT --to-destination 127.0.0.17:53
-A POSTROUTING -j LIBVIRT_PRT
-A POSTROUTING -s 10.0.3.0/24 ! -d 10.0.3.0/24 -j MASQUERADE
-A LIBVIRT_PRT -s 192.168.122.0/24 -d 224.0.0.0/24 -j RETURN
-A LIBVIRT_PRT -s 192.168.122.0/24 -d 255.255.255.255/32 -j RETURN
-A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -p tcp -j MASQUERADE --to-ports 1024-65535
-A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -p udp -j MASQUERADE --to-ports 1024-65535
-A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -j MASQUERADE
The sysctl net.ipv4.ip_forward shows the value is 1
The output of nft list ruleset is as follows:
table ip mangle {
chain C170 {
counter packets 329521 bytes 42983171 meta mark set ct mark
mark 0x0 counter packets 17735 bytes 2429935 queue num 17040 bypass
}
chain C171 {
counter packets 750958 bytes 581165784 meta mark set ct mark
mark 0x0 counter packets 77401 bytes 22111093 queue num 17140 bypass
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
counter packets 329521 bytes 42983171 jump C170
}
chain INPUT {
type filter hook input priority mangle; policy accept;
counter packets 750958 bytes 581165784 jump C171
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
counter packets 319891 bytes 41493267 jump LIBVIRT_PRT
oifname "lxcbr0" meta l4proto udp udp dport 68 counter packets 0 bytes 0 # CHECKSUM fill
}
chain LIBVIRT_PRT {
oifname "virbr0" meta l4proto udp udp dport 68 counter packets 38 bytes 12908 # CHECKSUM fill
}
}
table ip filter {
chain C17 {
mark 0x0 counter packets 2 bytes 272 drop
mark 0x6a4 counter packets 0 bytes 0 return
meta l4proto icmp mark 0x6a5 counter packets 0 bytes 0 return
mark 0x6a5 counter packets 0 bytes 0 reject with icmp type host-prohibited
mark 0x6a6 counter packets 204 bytes 6120 drop
counter packets 1076776 bytes 623890722 ct mark set mark
mark 0x6ae counter packets 959925 bytes 591009768 return
meta l4proto icmp mark 0x6af counter packets 54 bytes 4752 return
mark 0x6af counter packets 27 bytes 1620 reject with icmp type host-prohibited
mark 0x6b0 counter packets 78544 bytes 23162512 drop
mark 0x6b5 counter packets 0 bytes 0 return
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter packets 320184 bytes 41688472 jump LIBVIRT_OUT
counter packets 329481 bytes 42970183 jump C17
}
chain INPUT {
type filter hook input priority filter; policy accept;
counter packets 736720 bytes 567211499 jump LIBVIRT_INP
iifname "lxcbr0" meta l4proto tcp tcp dport 53 counter packets 0 bytes 0 accept
iifname "lxcbr0" meta l4proto udp udp dport 53 counter packets 0 bytes 0 accept
iifname "lxcbr0" meta l4proto tcp tcp dport 67 counter packets 0 bytes 0 accept
iifname "lxcbr0" meta l4proto udp udp dport 67 counter packets 0 bytes 0 accept
counter packets 747501 bytes 580926931 jump C17
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
ip daddr 192.168.122.103 ct state new,related,established counter packets 0 bytes 0 accept
counter packets 0 bytes 0 jump LIBVIRT_FWX
counter packets 0 bytes 0 jump LIBVIRT_FWI
counter packets 0 bytes 0 jump LIBVIRT_FWO
oifname "lxcbr0" counter packets 0 bytes 0 accept
iifname "lxcbr0" counter packets 0 bytes 0 accept
}
chain LIBVIRT_INP {
iifname "virbr0" meta l4proto udp udp dport 53 counter packets 3384 bytes 223947 accept
iifname "virbr0" meta l4proto tcp tcp dport 53 counter packets 35 bytes 1820 accept
iifname "virbr0" meta l4proto udp udp dport 67 counter packets 38 bytes 13086 accept
iifname "virbr0" meta l4proto tcp tcp dport 67 counter packets 0 bytes 0 accept
}
chain LIBVIRT_OUT {
oifname "virbr0" meta l4proto udp udp dport 53 counter packets 0 bytes 0 accept
oifname "virbr0" meta l4proto tcp tcp dport 53 counter packets 0 bytes 0 accept
oifname "virbr0" meta l4proto udp udp dport 68 counter packets 38 bytes 12908 accept
oifname "virbr0" meta l4proto tcp tcp dport 68 counter packets 0 bytes 0 accept
}
chain LIBVIRT_FWO {
iifname "virbr0" ip saddr 192.168.122.0/24 counter packets 0 bytes 0 accept
iifname "virbr0" counter packets 0 bytes 0 reject
}
chain LIBVIRT_FWI {
oifname "virbr0" ip daddr 192.168.122.0/24 ct state related,established counter packets 0 bytes 0 accept
oifname "virbr0" counter packets 0 bytes 0 reject
}
chain LIBVIRT_FWX {
iifname "virbr0" oifname "virbr0" counter packets 0 bytes 0 accept
}
}
table ip nat {
chain OUTPUT {
type nat hook output priority -100; policy accept;
meta l4proto udp mark 0x6b5 counter packets 0 bytes 0 dnat to 127.0.0.17:717
meta l4proto tcp mark 0x6b5 counter packets 0 bytes 0 dnat to 127.0.0.17:717
meta l4proto udp mark 0x707 counter packets 8350 bytes 604513 dnat to 127.0.0.17:53
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
counter packets 14300 bytes 1519659 jump LIBVIRT_PRT
ip saddr 10.0.3.0/24 ip daddr != 10.0.3.0/24 counter packets 72 bytes 17932 masquerade
}
chain LIBVIRT_PRT {
ip saddr 192.168.122.0/24 ip daddr 224.0.0.0/24 counter packets 34 bytes 3499 return
ip saddr 192.168.122.0/24 ip daddr 255.255.255.255 counter packets 0 bytes 0 return
meta l4proto tcp ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter packets 0 bytes 0 masquerade to :1024-65535
meta l4proto udp ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter packets 33 bytes 13696 masquerade to :1024-65535
ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter packets 0 bytes 0 masquerade
}
chain PREROUTING {
type nat hook prerouting priority dstnat; policy accept;
meta l4proto tcp ip daddr 192.168.100.4 tcp dport 80 counter packets 0 bytes 0 dnat to 192.168.122.103:80
meta l4proto tcp ip daddr 192.168.100.4 tcp dport 80 counter packets 0 bytes 0 dnat to 192.168.122.3:80
meta l4proto tcp ip daddr 192.168.100.4 tcp dport 80 counter packets 0 bytes 0 dnat to 192.168.122.2:80
meta l4proto tcp ip daddr 192.168.100.4 tcp dport 80 counter packets 0 bytes 0 dnat to 192.168.122.1:80
meta l4proto tcp ip daddr 192.168.100.4 tcp dport 80 counter packets 0 bytes 0 dnat to 192.168.122.0:80
}
}
table ip6 mangle {
chain C170 {
counter packets 2937 bytes 1017495 meta mark set ct mark
mark 0x0 counter packets 644 bytes 92091 queue num 17060 bypass
}
chain C171 {
counter packets 79076 bytes 27540091 meta mark set ct mark
mark 0x0 counter packets 75130 bytes 25982530 queue num 17160 bypass
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
counter packets 2937 bytes 1017495 jump C170
}
chain INPUT {
type filter hook input priority mangle; policy accept;
counter packets 79076 bytes 27540091 jump C171
}
chain LIBVIRT_PRT {
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
counter packets 4202 bytes 1496447 jump LIBVIRT_PRT
}
}
table ip6 filter {
chain C17 {
mark 0x0 counter packets 0 bytes 0 drop
mark 0x6a4 counter packets 0 bytes 0 return
meta l4proto ipv6-icmp mark 0x6a5 counter packets 0 bytes 0 return
mark 0x6a5 counter packets 0 bytes 0 reject with icmpv6 type admin-prohibited
mark 0x6a6 counter packets 0 bytes 0 drop
counter packets 81998 bytes 28555654 ct mark set mark
mark 0x6ae counter packets 7457 bytes 2613792 return
meta l4proto ipv6-icmp mark 0x6af counter packets 0 bytes 0 return
mark 0x6af counter packets 0 bytes 0 reject with icmpv6 type admin-prohibited
mark 0x6b0 counter packets 74470 bytes 25935586 drop
mark 0x6b5 counter packets 0 bytes 0 return
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter packets 2677 bytes 923453 jump LIBVIRT_OUT
counter packets 2922 bytes 1015563 jump C17
}
chain INPUT {
type filter hook input priority filter; policy accept;
counter packets 78566 bytes 27404953 jump LIBVIRT_INP
counter packets 79076 bytes 27540091 jump C17
}
chain LIBVIRT_INP {
}
chain LIBVIRT_OUT {
}
chain LIBVIRT_FWO {
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
counter packets 0 bytes 0 jump LIBVIRT_FWX
counter packets 0 bytes 0 jump LIBVIRT_FWI
counter packets 0 bytes 0 jump LIBVIRT_FWO
}
chain LIBVIRT_FWI {
}
chain LIBVIRT_FWX {
}
}
table ip6 nat {
chain OUTPUT {
type nat hook output priority -100; policy accept;
meta l4proto udp mark 0x6b5 counter packets 0 bytes 0 dnat to [::1]:717
meta l4proto tcp mark 0x6b5 counter packets 0 bytes 0 dnat to [::1]:717
meta l4proto udp mark 0x707 counter packets 0 bytes 0 dnat to [::1]:53
}
chain LIBVIRT_PRT {
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
counter packets 245 bytes 62982 jump LIBVIRT_PRT
}
}
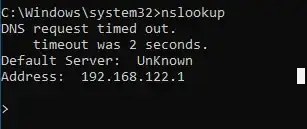
ADDENDUM 3: The output of nslookup in the guest machine: