I finally got it working. This is for anybody who wants to achieve the same as me.
Install Ubuntu, install Wireguard server.
Create a wg0.conf using your VPN provider's configuration. In my case, I had to use this python script https://github.com/hsand/pia-wg to extract PIA WireGuard configuration. My wg0 configuration looks something like this:
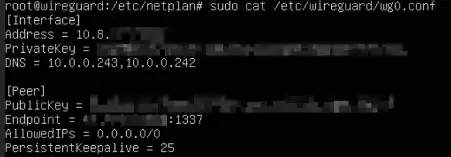
Test VPN connectivity, if everything works, you can continue.
Next, enable IP forwarding, I used this post: https://linuxconfig.org/how-to-turn-on-off-ip-forwarding-in-linux. At this point, I tested that forwarding works, by setting my Wireguard VPN as the default gateway for my w11 test VM (Your VPN tunnel needs to be disabled for now, as the forwarding with that isn't configured yet). Tracert to google.com shows that Wireguard VM is one of the hops, so everything works.
Next, I changed my virtual machine NIC’s name servers to use PIA DNS servers (Can be found on their website or copied from wg0 configuration https://helpdesk.privateinternetaccess.com/kb/articles/using-pia-dns-in-custom-configurations). I’ll explain later why I did this. NIC configuration:
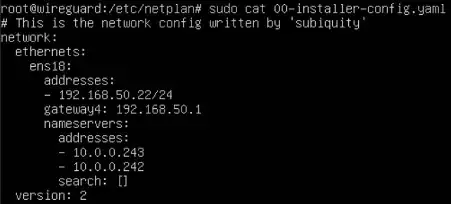
Next comes the main part which makes this all work, IPTABLES configuration. I got an already made script from Craft Computing YouTube channel (https://youtu.be/xFficDCEv3c), modified some settings to fit my use case. See the sections which begin with "CHANGED", those are the settings I changed.
https://pastebin.com/H2yrqXMF
I saved iptables.sh in my /etc/wireguard/ folder.
Next, enable your WireGuard tunnel and run the Iptables script using sudo bash iptables.sh . (This broke my SSH, but I didn’t mind as I control the server from Proxmox console.)
Why use PIA DNS servers?
When testing this configuration for DNS leaks, I noticed that my machine still used my IPS’s DNS server, effectively leaking my public IP. This is why in step 5 I changed the DNS configuration of the VPN VM and also the DNS settings of the machine which is routing its traffic though VPN.
How I use this:
On a machine I want the traffic to be routed through WireGuard VPN, I set the default gateway to the address of my WireGuard VM and DNS servers to PIA’s DNS servers.
I don’t know if this is the best way to do this, but this works for me.
About the IPtables
They are set up in a way if the VPN tunnel goes down, no traffic will be redirected. Essentially acting as "Kill Switch".

