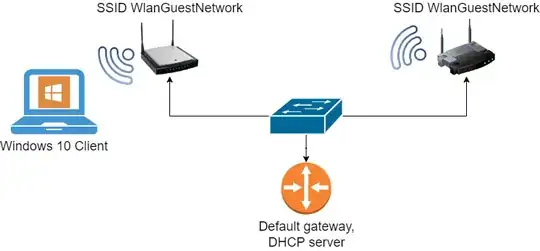
I have some questions and assumptions and I want to ask about them: Based on topology in my picture: Assuming situation 1: APs are configured just as APs with WPA3 Personal, they don't know about each other anything.
Windows 10 client comes to the left AP for the first time, it signs in to the network WlanGuestNetwork for the first time.
Will client moves from coverage of the left AP to the coverage of the right AP - it will not connect to WlanGuestNetwork of the right AP, because of different BSSID? What if attacker makes a similar to the left AP, that will also copy BSSID of the Left AP, will client try to auto reconnect to fake AP or there is some sort of protection going on? If it will try to connect, will there password be exposed, or is there some fancy hashing system that will prevent it?
Situation 2. If we want client to seamlessly roam between those 2 APs the only wired solution is to implement MESH network with some manufacturer provided standard, this means that we need controller, for enterprise devices there will be hardware controller and for consumer devices one AP will act as a controller?
Now WDS is wireless only interconnection, because it needs support from AP interconnecting protocol, and 802.11 has some 4 mac address support and so on, while MESH can have both wired and wireless backbone, but logic behind AP interconnection in both case fundamentally different? Is there MESH APs, that have wired/wireless backbone failover, e.q. if you cut the cable, stations will still be connected wirelessly?
With mesh, roaming switching quality is entirely on the client, only some APs have support to drop clients with low signal, forcing them to sihti and latest 6E standard has something to improve this?