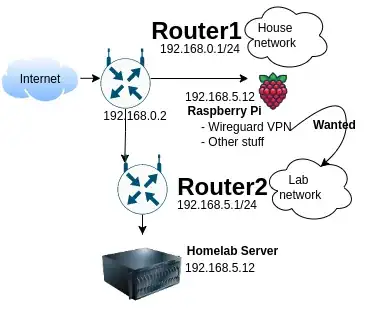
I have a router (R1) of my ISP on 192.168.0.1, it gives the second router (R2) the ip 192.168.0.2 and is connected lan to wan port.
R2 is an archer c20 and has the network 192.168.5.0/24, it's on 192.168.5.1
I can access the R1 LAN from R2 but not to access the R2 LAN from R1. I reviewed a few questions here but I'm not clear why it's not possible or if there's a workaround.
I thought that if I do sudo ip route add 192.168.5.0/24 via 192.168.0.2 when I ping 192.168.5.1 it will work because router 2 knows his network but it doesn't work.
Is there a way to get to the second's subnet from the first?
Update:
There were three goals: to isolate the two networks, to have only one service (a vpn) on the first network who can access to the second one (to do a wakeonlan), and to make a subnet to scape from overlaping subnets on vpn without touching isp R1 LAN.
But the first network is still reachable from the second one because it's the main gw, so it doesnt' work as I expected to protect my home network, probably I'm moving to switch my router mode to an AP, and to limit the vpn to some devices only.
Conclusions and notes learned:
Finally the R2 network could be reachable from lan on R1, the issue was with the firewall as pointed @user1686, I didn't see that the router has an option in security "Enable SPI Firewall", dissabling it solves the issue, that's why I selected that answer.
From there you need to add a static route in the router or in this case only in the dessired devices like sudo ip route add 192.168.5.0/24 via 192.168.0.2 (and dev wlan0 if it's necessary), make sure it's all right with route -n or ip route get 192.168.5.12 and a ping. Then you can make it persistent in a file /etc/dhcpcd.exit-hook
Added the static route, I can ping to inners LAN ips, I can't ping R2 on its WAN or in its local ip but that's a default option router's restriction. But I couldn't get into its admin on 192.168.5.1 from a browser, a bit odd.
DOUBLE NAT
BUT as pointed by @harrymc it's an overly setup, and @davidgo led me to a research about this case.
This is a case of double NAT, for most users it won't be noticiable, but on some games consoles or to expose services, it will add an overhead:
For example, if I had a page in the innner router, there are 3 options: open port 80 twice (PAT), make R2 a DMZ, or to add a static route there (if R1 has the option).
The primary goal of isolating the main home network is not possible (is still reachable from R2) and the management of the routing is complex.
Therefore, it's not a good solution to use double nat as a firewall (check double nat and double nat forum). And security still depends on which ports are exposed, wich services and passwords are used.
SOLUTION
So if you are double natting, don't.
- Put R2 as an access point, disabling its dhcp, and keep R1 to manage the ips. (LAN to LAN recommended, or LAN to WAN in AP mode) (and if a vpn is wanted, check the network setup to solve overlap issues).
- Option two if you want full management, put ISP R1 on bridge mode, and make R2 the main router.
Thanks to all