I have a ZTE (F670L) router for my home network. Since past few days, I have been observing SSL certificate error (NET::ERR_CERT_AUTHORITY_INVALID), occurring abruptly more frequently than before. This initially started happening with Firefox (version 112.0.2), and all the websites that wouldn't open with Firefox, would open just fine with chrome (version 112.0.5615). But a few days later, this started happening with chrome as well as with edge browser! Now this happens for websites across the spectrum range (academics, marketing, sports, news etc.), barring a few ones such as, say, Wikipedia or www.google.com maybe. Also, this happens on all of my devices such as laptops, tablets and mobiles and with Windows as well as Ubuntu.
Interesting thing is, if and when I switch to a different network at that time, (say a data network on my mobile or a WiFi via a hotspot from my mobile data), all the websites seem to open correctly. Another important thing I have noticed is that, usually when there is an SSL certificate error, there is an option of an "advanced" button, which takes the user to the website at "their own risk"!. But if I try to force my way to any website in the context of my present issue, a lot of random pages start opening (e.g. I usually land at some random betting or other advertisement webpages!), instead of the required one. Also, if I try the open the website from the google search result page several times (usually say after trying more than 9-10 times, going back and again clicking the website link), the correct website is served to me (with all the security certificate with correct validity!). Last important point is that very old normal html pages (non-HTTPS) are also not available to me now!
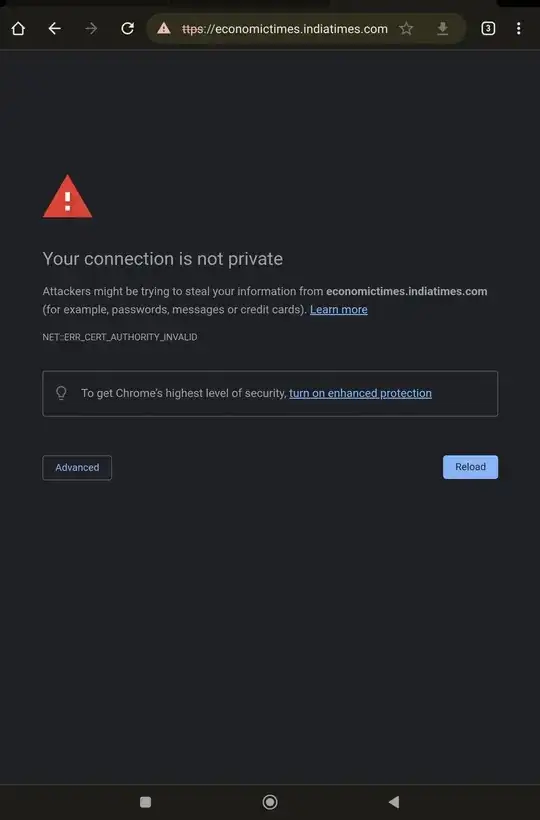
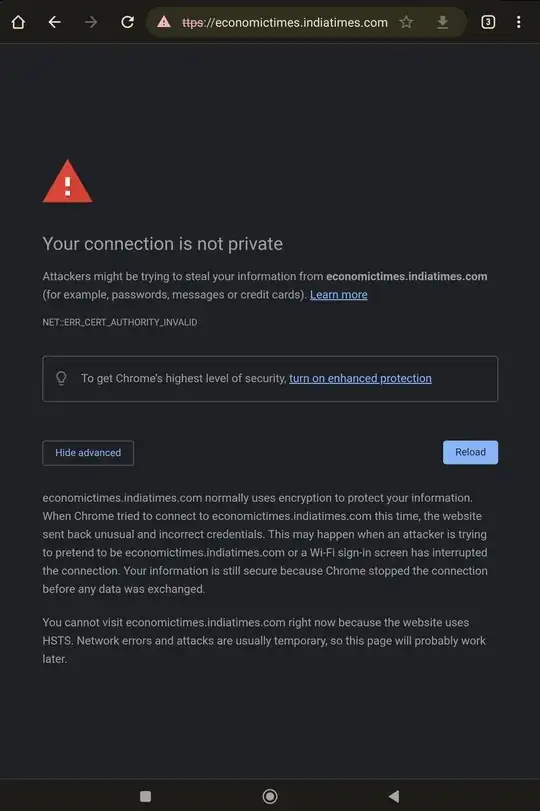
Few months ago, I tried to expose my router for attacks (port 22 and 23) for a honeypot on one of my machines (typical Cowrie implementation, using one of my virtual machines as honeypot and another virtual machine as the proxy back end ... nothing fancy!). This has started happening after a long time (maybe 3 months) since my honeypot experiment. I am attaching two screenshots of the certificate error against one of the famous news websites in my country (India). I have not found any extra IP address in my router. The router firmware seems proprietary, and is managed by TR 069 protocol. Interestingly, among the IP addresses from across the globe that attacked my honeypot, I found a few IP addresses from the same ISP whose services I am availing!I wanted to know if there is a sure way to figure out if the problem pertains to my router possibly being compromised, or is it something else? I hope I have supplied all the required information!