I need to provide some proof for the judge on a pendrive. I bought new 32GB pendrive and would like to upload 8MB file on it and make the pendrive read only forever, so nobody tampers with it. Is it doable?
11 Answers
Alternative solution:
Burn the file to a CD-R or DVD-R disc. This is pretty much the easiest and most tamper-proof way to save a file 100% read-only.
- 2,306
I don't know of a way of making a removable device read-only in a tamper-proof way, but here is a suggestion based on the most prevalent method now used for validating files - checksum.
Add to the disk some software that does a good checksum of your files and ensure that the checksums of the files are calculated by this software and are well-published together with the files.
The checksums of the files can then later be verified to show that the files have or have not been tampered with.
- 498,455
EDIT: I misread the question, for intended purpose I think harrymc's answer is better suited:
- In digital forensics 'hashing' (of files, entire drives and disk images) plays a vital role.
- What is important is that the source for the data isn't modified, so this needs to write protected any time it's accessed. A forensic specialist will typically use a hardware write blocking device.
- The source is hashed and then the evidence taken from it is hashed. * If we talk about a file, the hashes of the original file and the one on the flash drive you intend to present in court need to match.
- This (the identical hashes) proves evidence was not tampered with and whether that stick is read only or not is irrelevant.
My answer is still valid for write protecting USB flash drives.
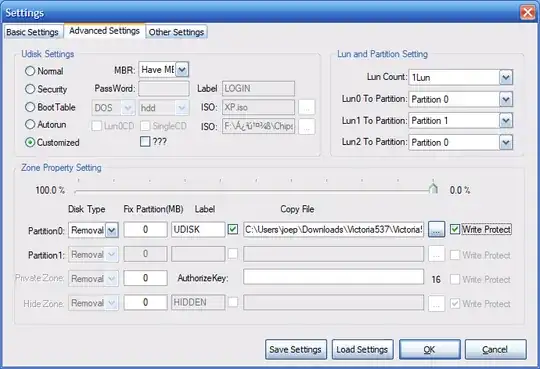
Do-able, yes. You'd need to use an MPTool (mass production tool) and reconfigure the firmware of the drive. MPTools are pieces of software made available by manufacturers you can use to configure USB flash drives firmware.
Now that sounds all easy but there's bears:
- You'd need to determine the specific controller for the USB flash drive as these MPTools are controller specific.
- For most of these tools you'll have to find your way through either Chinese or Russian websites
- You'll find that finding the right tool in itself is difficult, but that your virus scanner will not like many of the downloads offered on these website either.
But then it should be possible to make a write-protected USB Pendrive containing your file(s).
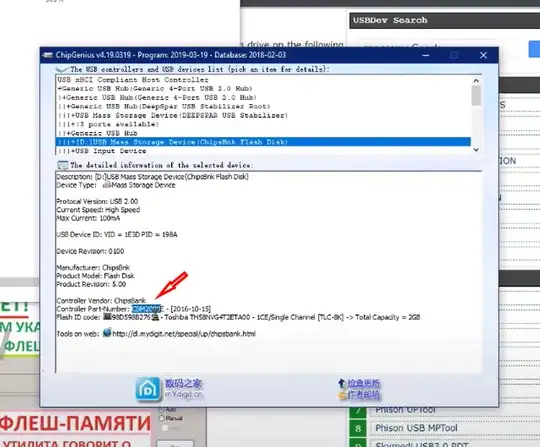
- To determine controller, you can use the tool ChipGenius (check for malware before using). You will have to search for it, as there would be a good chance I'd directly link you to malware, which I don't want to do.
- For my own experiments I used the website
https://www.usbdev.ru/ - I recorded some of my steps here: https://youtu.be/yIuK6goBj8g
ChipGenius tool will give you the controller:
For which you try find a matching MPTool:
Final words on this, many website offer customizable USB Pendrives, so you can ask them to provide you with write-protected drives containing your content.
To answer the XY problem, you don't. Preventing the drive from being written to is not even useful in thwarting someone who wants to forge the contents, because they could just replace it with an identical-looking flash drive that wasn't write-protected.
The way you solve this problem is by putting the files in some kind of archive format (like a zip file) on the storage medium, and submitting with it a strong cryptographic hash (e.g. sha256) of the archive file as a notarized paper document with your signature and the notary's signature/stamp on it.
The iStorage datAshur PRO2 64 GB encrypted USB flash drive (https://a.co/d/1CUAy7w) -- and I assume other capacity variants -- support a mode where the drive may be set to read-only (and only knowledge of the administrator-mode PIN can change the setting).
See table of contents at https://istorage-uk.com/wp-content/uploads/2019/05/datAshur-PRO2-user-manual_v2.5hl.pdf
Also, the Apricorn Aegis Secure Key 3.0 encrypted USB sticks seem to have comparable features (https://a.co/d/9KYDMtd).
See table of contents at https://apricorn.com/content/product_pdf/aegis_secure_key/usb_3.0_flash_drive/ask3_manual_configurable_online_2.pdf
There are probably others as well.
- 31
SD cards support temporary and permanent write protection (that is digital and completely independent of the switch on the full-size cards). https://github.com/BertoldVdb/sdtool is an example of a tool that can do this.
But, as others have also stated, the easiest method for making the data tamper-proof is calculating and submitting its hash too, or if you can, digitally signing it.
- 265
You don't need a technical solution here. In order satisfy the legal criteria (chain of custody) you don't need to make it absolutely technically impossible for changes to occur, you just need to be able to show that it hasn't happened.
Seal the USB inside something, like a sealed envelope. Send it to the judge. When they open it the judge knows nobody has tampered with it between it leaving you and reaching him. That is all you need to show, and all you can show. No amount of "read only" technology can guard against tempering by you (I.e. you deliberately sending the wrong data) and it's assumed the judge won't tamper with it. (If he would then there are much bigger problems).
Simultaneously keep a copy of the data yourself so that if a question arises you can compare it with your copy. You are going to be asked to testify about the provenance of this evidence anyway, so if a quick comparison test will allow you to say "yes I'm sure that's the data I sent" that will help.
If this is a legal thing you are going to be asked if this is the correct data, since you provided it. Nothing else will satisfy the law.
- 147
Simply send the Pen drive wrapped in a sealed envelope with "TAMPER" evident tape on the join, and perhaps holding the cap on. Hand-deliver it to the judge's office and get a receipt.
Separately, email the same file.
Separately, post a printout in the regular mail.
Finally when/if you go to court, take your own printouts as well.
This presumes the documents are not secret/confidential. Consider that the judicial process is not out to get you. Instead of worrying that the judge's team as an enemy, work on preparing your case to be watertight.
If you or your rep DID spot an inconsistency during proceedings, then raise an objection and handle it there.
Some label printers can use tamper-evident tape to make labels. Many of these tapes will say "void", which would be perfectly adequate.
- 2,580
What you actually want is something like an image file with a checksum. You can also link it to one of the crypto blockchains, giving it a date that can't be refuted. But the judge probably can't even use his email without help ... The tools exist; no one knows how to use them. In steps third party sending and sign services, like DocuSign. That route is probably best.
- 805
The solution you're looking for is cryptographic signature by you (it identifies you as a certifier of authenticity), and a secure time-stamp (proves that the signed file existed at the time of stamping). The recipient can use independently verify that the secure stamp is valid (ie, the object has not been tampered with).
You could/should include a README that explains how secure timestamping works, in case the judge is not tech savvy, so he doesn't need an expert witness to verify the timestamp.
A USB drive can be replaced with another, identically looking, but with different contents. A tamper proof envelope can be replaced with another.
The CD-ROM can be attacked in the same way, by replacing the CD-ROM with a fake.
If the adversary has the opportunity to attack the authenticity of your evidence (and if the court is not completely corrupt), they can find a flaw in your technique and create reasonable doubt that the evidence is not authentic.
- 161
I had a USB pen drive back in the days of old which was 32 Mbytes, USB1, and so physically big that it came with an extension cable just to reach the socket.
However it also had a small write-enable switch on the side of the pen drive. Assuming you could find something like that with a hardware switch, then write your file and use epoxy to (neatly) lock the switch in place. You could also use a soldering iron to melt the plastic.
That might be ugly, so a higher level would be to write your file and a separate MD5sum file, then open the pen drive and either short or bridge the switch so its stuck in the Write Protect mode.
The workaround would be to undo your soldering, but any miscreant would have to know it is there.
- 2,580