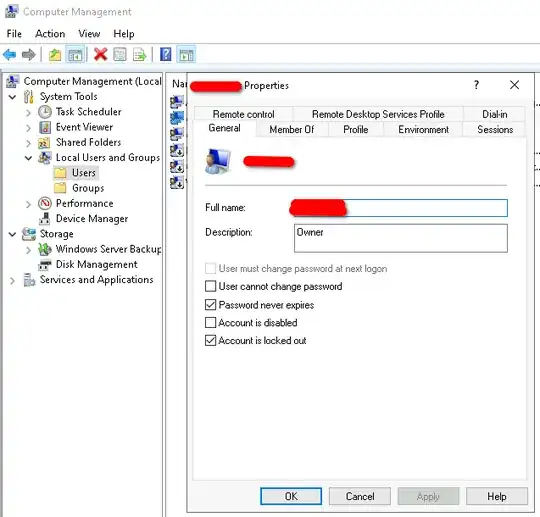
There's a Windows Server 2022 with two administrator local users. This is not Active Directory topic. One of the admins got locked out. I go ahead and uncheck the locked out status in the Local Computer Management's Local Users and Groups, and Apply it. It seems to be Applied when I look back immediately.
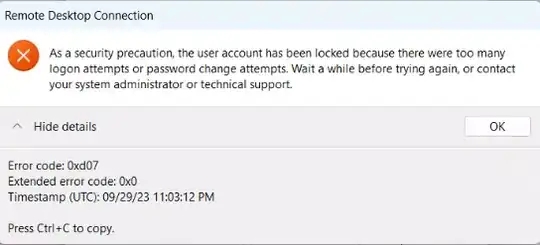
However if I do anything else and I check it again, or that local admin user tries to log in via RDP (both of us access the box via RDP) the locked out checkbox gets check again.
How the hell on Earth can I get that checkbox stay unchecked and let the other admin login? I'm pulling my hair out.
I'm trying now a shell command:
net user "theusername" /active:yes
We'll see if that helps (I think it won't)
For the command above: the active status is not the same as locked out or not. To show more details to questions. The accounts:
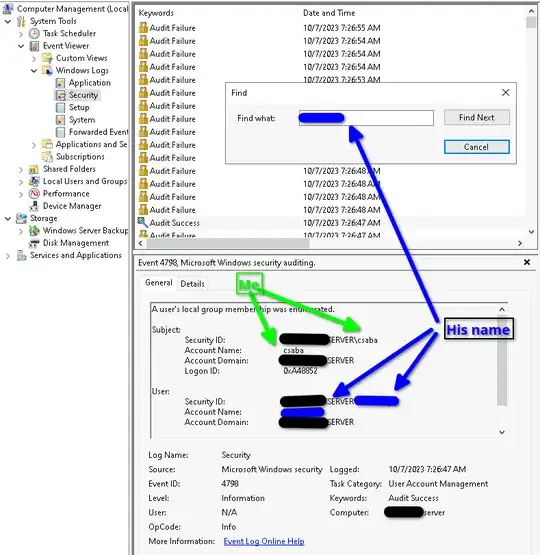
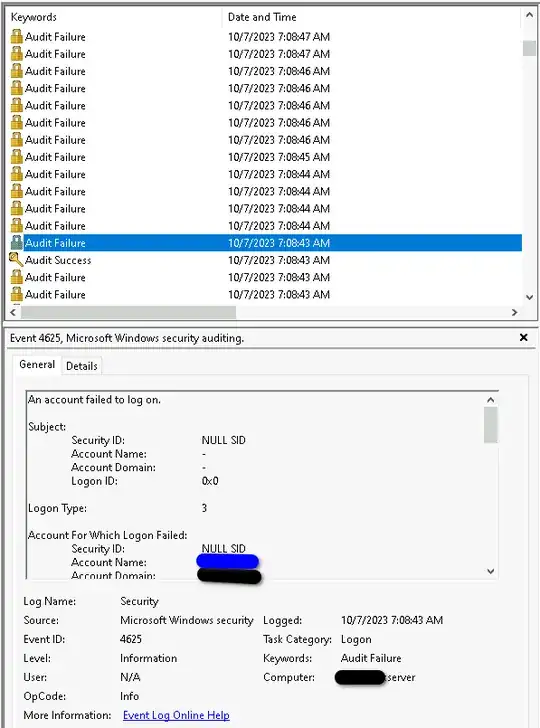
When I successfully login or do something:
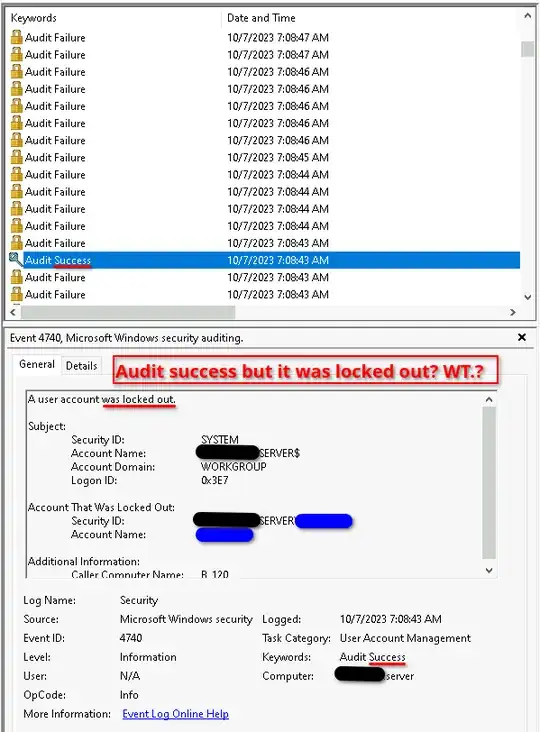
When things fail:
And I'm sure that this wasn't a login attempt by him. Rather it's some process? It is even spurious if something is compromised, however I don't see anything with Process Explorer, and the box is up to date. As you can see bots are constantly trying to get in but those are standard names they try.