I found the way:
Install XCA from Windows Store:
(as of 24/11/2023, v2.5.0 uses OpenSSL v3.1.2.1 from August 2023)
Prepare a clean USB Stick for XCA database → Run XCA
Create a new database on the USB Stick: Home.xcd
The database is password protected, so it is necessary to choose one for future use
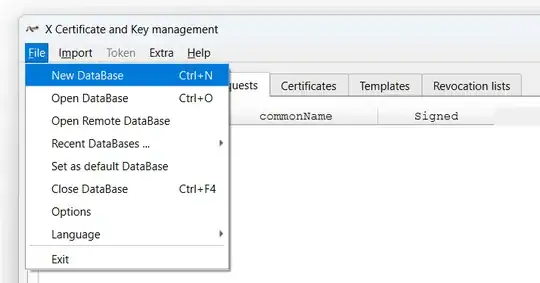
Tab: Templates
XCA has four default templates for any arbitrary, non-specific use case
[default] Empty template[default] CA[default] TLS_Client[default] TLS_Server
New tepmlate & Change template → Edit XCA template dialog
For IPSec certificates, I generated three new templates
IPSec_CA_Template (inherited from 4.2)IPSec_Client_Template (inherited from 4.3)IPSec_Server_Template (inherited from 4.4)
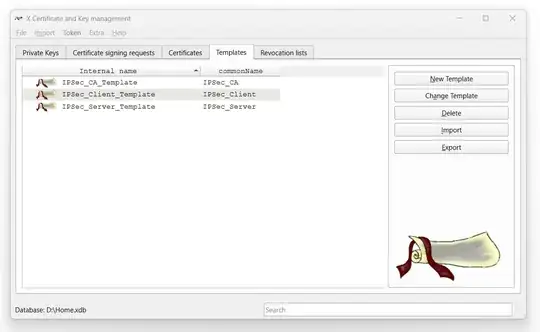
Tab: Key Usage
Select Key Usage (KU), Extended KU (EKU), and critical (optional)
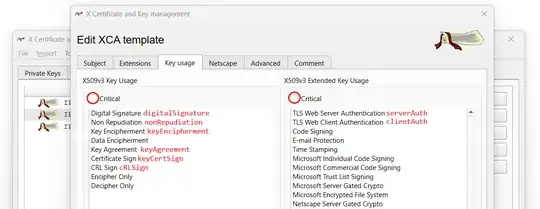
CA:
keyUsage=critical,digitalSignature, keyCertSign, cRLSign
Client:
keyUsage=critical,digitalSignature, keyEncipherment
extendedKeyUsage=critical,clientAuth
Server:
keyUsage=critical,digitalSignature, keyEncipherment, keyAgreement
extendedKeyUsage=critical,serverAuth
Tab: Subject
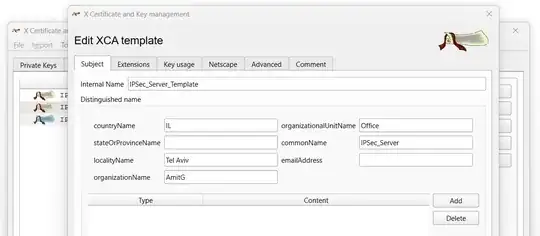
Tab: Netscape
Unselected all and deleted the comment
Once the customized templates are ready - This is the start point, for any new certificate
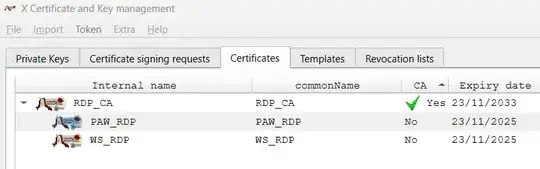
Create New Certificate
I adhered to the Creating certificates with XCA manual of Fortinet for the creation of the certificates but with the customized templates from section 5. Since the customized templates contain all the data, including Subject and Extensions, it is necessary to click Apply All instead of Apply Extensions as written in the manual. Example for Server Certificate:
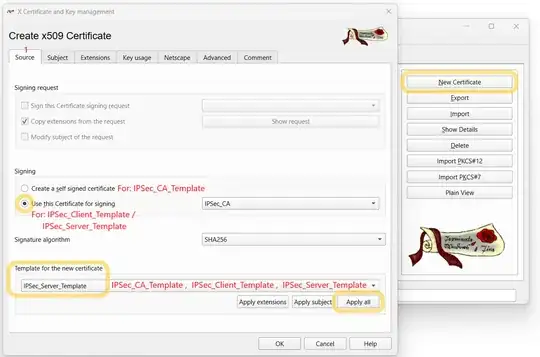
[For Client / Server certificate. Not for CA]
(2nd thing after tab Source) The only thing that is not in the template is the X509v3 Subject Alternative Name. It should be entered specifically with the hostname and the domain of the entity for whom the certificate is issued.
Since it is a DHCP-enabled environment, fixed IPs are not assumed, and instead, a hostname.domain syntax is used. Refer to the appendix for information about configuring local-domain.
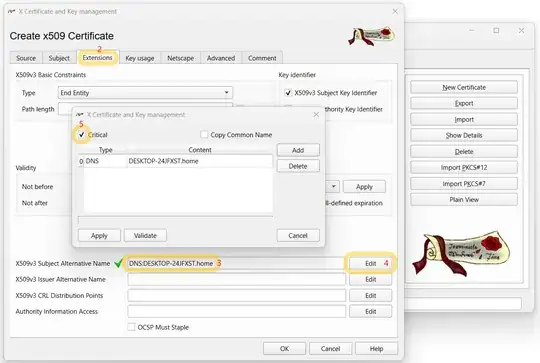
Resultant V3 Profiles:
Here are the X509v3 extensions (in compare with this reference)
CA: (The reference has also: authorityKeyIdentifier)
basicConstraints=critical,CA:TRUE
keyUsage=critical,digitalSignature, keyCertSign, cRLSign
subjectKeyIdentifier=hash
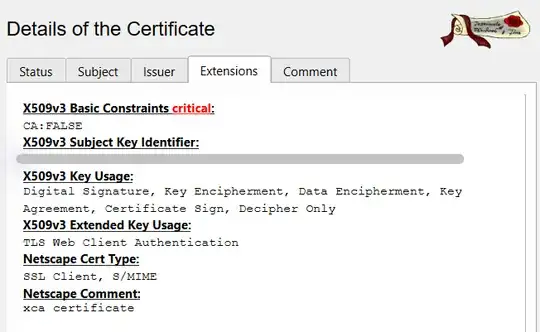
Client: (The reference has also: authorityKeyIdentifier, nonrepudiation (KU))
subjectAltName=critical,DNS:DESKTOP-KGXWQ2R.home
extendedKeyUsage=critical,clientAuth
keyUsage=critical,digitalSignature, keyEncipherment
subjectKeyIdentifier=hash
basicConstraints=critical,CA:FALSE
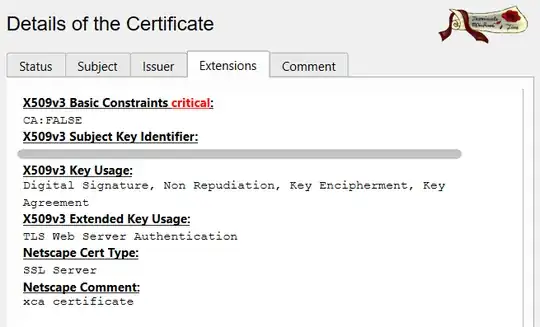
Server: (The reference has also: authorityKeyIdentifier, nonRepudiation(KU))
subjectAltName=critical,DNS:DESKTOP-24JFXST.home
extendedKeyUsage=critical,serverAuth
keyUsage=critical,digitalSignature, keyEncipherment, keyAgreement
subjectKeyIdentifier=hash
basicConstraints=critical,CA:FALSE
- Based on the comments below,
authorityKeyIdentifier "is usually not mandatory" and nonRepudiation "is not used for any network protocol".
Appendix: Local Domain
For the local domain home I had to configure my router (that accepts on that field only a-z and - chars):
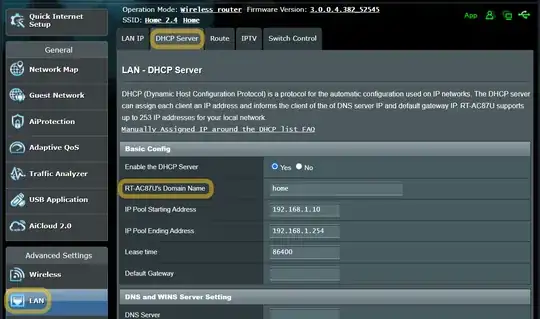
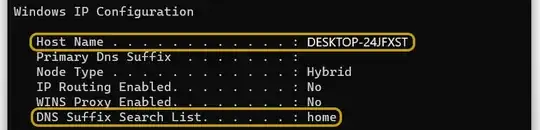
To verify whether the computer is within the home local domain, open cmd.exe and enter:
ipconfig /all
As desired: