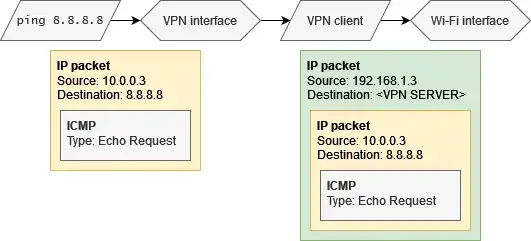
I have a local machine on a VPN network with private IP A , and a VPS with private IP B which acts as an exit node, i.e. all traffic in the local machine is supposedly being routed from the local machine encrypted to the VPS which then routes it to the final public destination.
I was trying to find out if my VPN was leaking so I span up Wireshark and had it listen on the virtual interface created by the VPN and filtered by ip.addr != B
I would expect to only see DNS requests there, but all BitTorrent traffic shows up as well. I can see packets with source/destination as A -> <Public IP> and vice-versa
It's clearly leaving via the interface and using the local machine's (macOS) private IP address A, but looking at the WireShark output it seems to not pass through the VPS.
Weirder still, if I use ipleak.net I don't see any leak, the torrent address comes out as the public address of the VPS.
Am I just interpreting the output incorrectly?