Update: today I found some decisive evidence on its misbehaviour. Sandbox analysis from VirusTotal on its installer reports video capturing capability using webcam.
See the link to its analysis here.
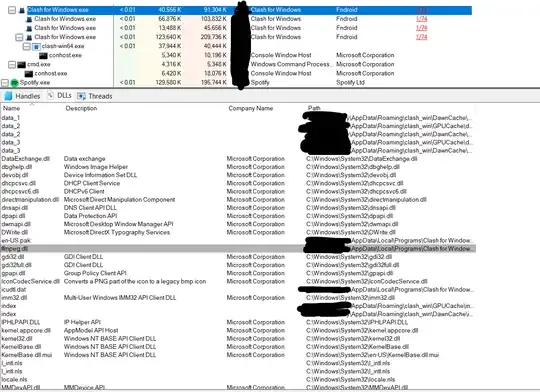
I recently found that a proxy program (Clash for Windows) that I installed on my Windows PC always links to DLLs that are unrelated to its function.
It has DLLs of FFmpeg, DirectX, OpenGL, and Vulkan in its installation directory. And through Process Explorer, I confirmed that it indeed loads such DLLs (Always FFmpeg, but not always all of the other three).
As I mentioned, it should only serve as a proxy program, and the only legitimate reason (that I can think of) why it loads the DLLs of low-level graphics APIs is for hardware acceleration of its UI -- but I have not found related settings in it. Most importantly, I cannot think of a reason to justify its loading FFmpeg.
FFmpeg is known to be able to stream videos to a remote client, and I suspect that the program is spyware -- that it uses the low-level Graphics APIs to capture the screen and stream it via FFmpeg.
That of course is my speculation. So my questions are,
- Can the DLLs it loaded be used in other legitimate ways that I have not thought of?
- Is there any way to investigate it further to obtain decisive evidence on its being spyware?
- The program has only run as a Normal User on my PC. If it was indeed spyware, how much damage could it have caused, and how could I possibly mitigate from the damage (e.g. What kinds of backdoors could it have left as a Normal User)?
I sincerely appreciate any insight you provide and your time in advance.