I'm using OpenWRT 23.05 and I have following situation:
- Local server in network
lan, accessible via port 80, 443 on IP10.150.42.7 - My PC, on the same network
- My Phone, on the same network
- My sister's phone, lives somewhere else
I gave my sister access to the server mentioned above using Tailscale. I have set up a public DNS record which points to the Tailscale IP 100.76.72.54. I have also configured HTTPs using Caddy on the server.
This way my sister can access the server via Tailscale and just has to enter the public domain name which works fine.
The domain name I use locally and in the public internet is the same and I wish that to stay that way. I am not going to configure a second domain, otherwise I have to keep changing the configuration on my portable devices.
On my OpenWRT router I have configured that the DNS name should be resolved internally to the internal IP 10.150.42.7, which works fine (I tested it with dig).
However, the problem is due to DNSSEC being enabled in the browser on my PC, it does not use the internal resolver and rather forcefully uses the public DNS resolver and thus gets the Tailscale IP. Since my PC is not connected to Tailscale at all times (and I don't want to change this) and I also don't want to disable DNSSEC on all devices in my network, I want to rewrite the IP in OpenWRT.
How do I configure OpenWRT (LuCI preferred) so that the destination IP address 100.76.72.54 is rewritten to 10.150.42.7 in the network lan?
I have tried following things:
Port Forward
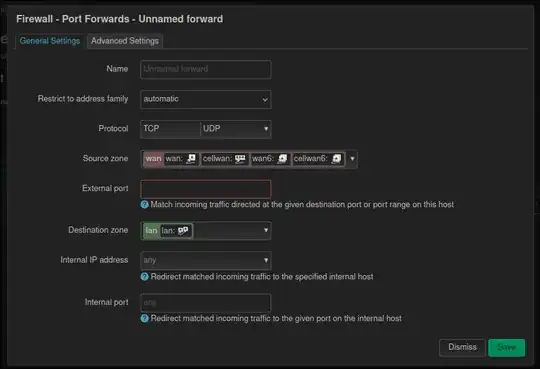 But here I can only specify where to route the traffic to but not what the "original" IP is, so this would just redirect everything.
But here I can only specify where to route the traffic to but not what the "original" IP is, so this would just redirect everything.
Traffic Rules
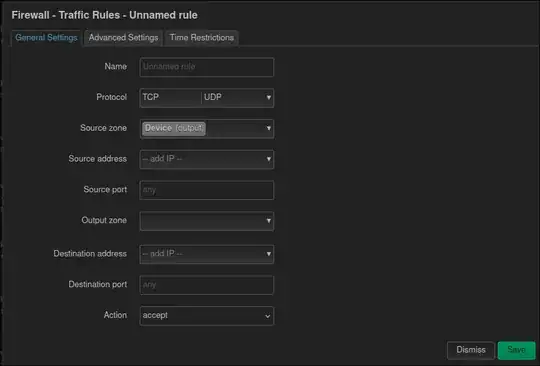 I can't specify "forward" in "Action" so this is not the right place.
I can't specify "forward" in "Action" so this is not the right place.
NAT Rules
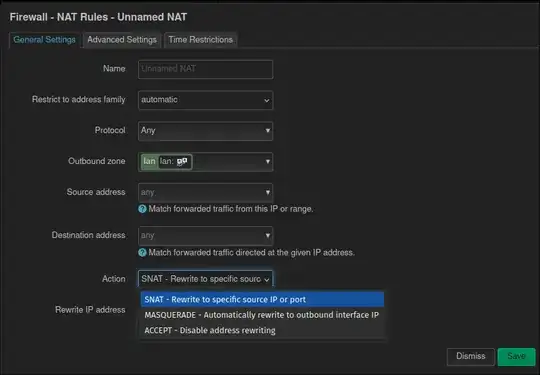 Here I can specify a "Rewrite IP address" but there is no "DNAT" choice in "Action".
Here I can specify a "Rewrite IP address" but there is no "DNAT" choice in "Action".
Static route
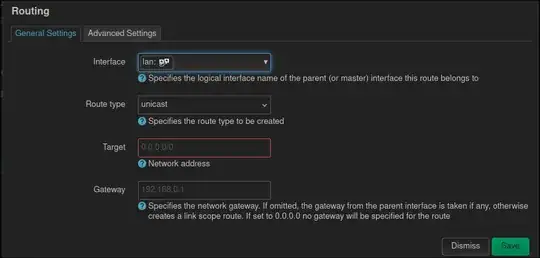 I can specify the IP address (using /32) and the Gateway but it won't actually rewrite the destination IP address but rather just route it to the Gateway which has no idea what to do with it (which is already the case since the 100.* addresses would have no destination in the first place)
I can specify the IP address (using /32) and the Gateway but it won't actually rewrite the destination IP address but rather just route it to the Gateway which has no idea what to do with it (which is already the case since the 100.* addresses would have no destination in the first place)