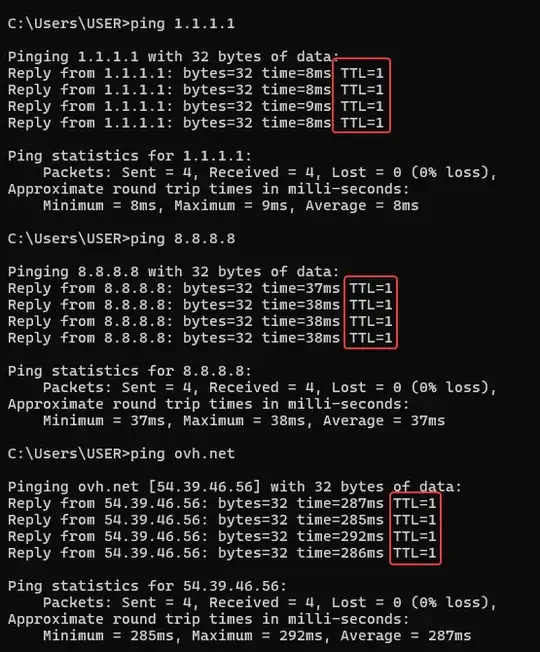
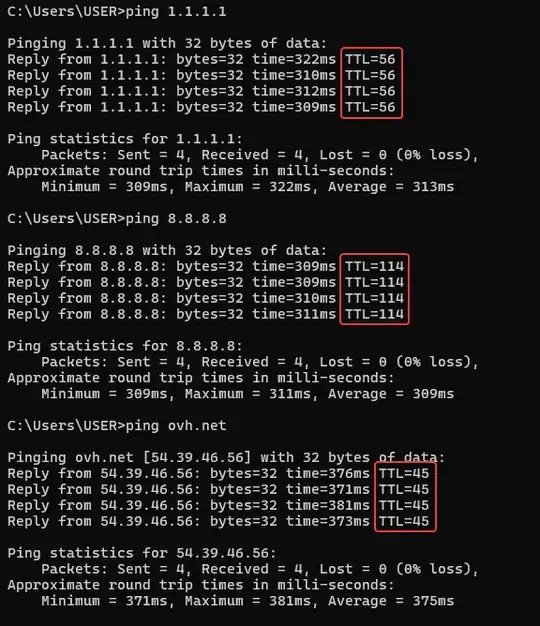
Can packets be "wrapped"? Like the incoming packet has TTL=1, comes to my wireguard interface, but after it is unwrapped by the wireguard interface, it gets a new TTL. Any resource on this "wrapping" will also be helpful.
Yes, and such wrapping (more commonly called 'tunneling') is literally the purpose of WireGuard, or indeed the purpose of pretty much any VPN software1. It's what makes it possible for the VPN's network interface to have its own IP addresses invisible to the outer network – and since the TTL is part of IP, by extension it becomes possible to have a TTL that's invisible to the outer network as well.
The packet's original TTL is not actually altered by WireGuard; rather, it produces a packet with two TTLs – and two IP headers in general – the original "inner" header from 'ovh.net' and the "outer" header from your WireGuard server. Sending a packet through VPN software causes it to generate a new packet with an additional IP header over the original, and vice versa. (In case of WireGuard there are also additional UDP and WG headers, but that's somewhat besides the point; direct IP-in-IP would be equally possible.)
In your case, your ISP is only able to change the TTL of the outer header, but not the inner one from ovh.net. So when the wrapped WireGuard UDP packet (with TTL=1) is received by the OS, it is unwrapped by WireGuard and the original ICMP Echo packet (with TTL=45) that was inside is re-injected to the OS where it becomes visible as the ping response.
Wireshark could be used to inspect this visually; it cannot see through WireGuard's encryption, but it could see through unencrypted tunnel types such as GRE or IP-in-IP – take a look at some collected example captures.
1 (Except for "SSH tunneling" and browser-integrated VPNs; both of those are really higher-layer proxies, so they don't deal with TTLs directly. The term 'tunneling' still applies to them, but with a slightly broader meaning of putting one protocol inside another same-layer protocol, in general terms – e.g. "HTTP inside HTTP" or "HTTP inside SSH" – rather than specifically being "IP packet inside IP packet" as with WireGuard.)