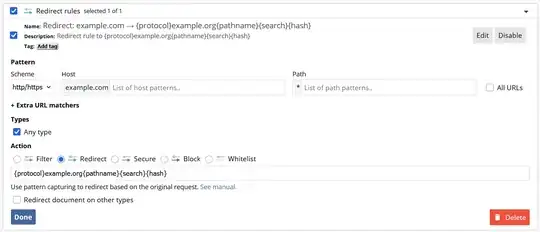
There's a site I frequently visit that makes use of several CDN domains and subdomains. One of these CDN subdomains recently stopped working for some reason, and it is affecting others, not just me.
I noticed that requests for:
https://subdom_1.dom_1.com/somefile.png
are failing (nothing is served), but if I change the FQDN to:
https://subdom_2.dom_2.com/somefile.png
the file gets served correctly.
I want to avoid installing a browser extension, so I was thinking there might be a way to do this maybe via /etc/hosts (I'm on linux). Ample searches didn't give me the answers, but hints such as using /etc/resolv.conf or dnsmasq or using 0.0.0.0 subdom_1.dom_1.com subdom_2.dom_2.com in /etc/hosts came up. But the manuals were less than clear, and I rather not risk opening up some security hole into my machine by doing something I don't fully understand.
Anyone have any clues as to what I can do? Refs to manuals and explanations of security concerns, etc, would be greatly appreciated.