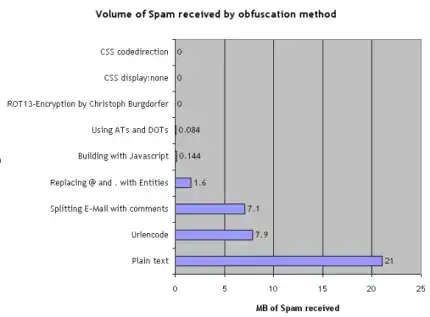
Yes it is true in most cases because you need a pattern for email harvesting, the more complex the pattern the more expensive (time/money) it is for spammers to work at getting emails. Of course nothing stops manual harvesting, but that is very low. The thing that is usually done is non JS encoded, plain text emails are harvested (check any 1-2 year old website that is unchanged, and I bet you $20 bucks its plain text email and they get tons of spam).
At my company all the external facing emails are obfuscated using a series of server side & JS client side methods.
So an email never really looks like an email, and the pattern ALWAYS changes. You would be surprised how well this method works, sure some methods are compromised and easily broken, but more elaborate methods of email obfuscation usually make the harvesting pointless as the sheer amount of pattern detection would require a lot of invested resources.
Brute force of CAPTCHAS is different, where the hackers/spammers/harvesters TARGET a specific site. This does not really apply to small mom & pop websites who might use a myriad of obfuscation methods, or sites where users post different format emails in a variety of email obfuscation ways (omitting the .com or .net, etc).
Most harvesters are not Javascript aware, that is they do not process JS. Making those methods more costly for harvesters. There are some harvesters that do try to process JS, but like I said it is very costly when you are running millions of emails in a matter of minutes, you don't want to go down to 10s or 100s if you can do 1000s.
My method of doing an each time random method works very well, I have yet to get any spam on my account.