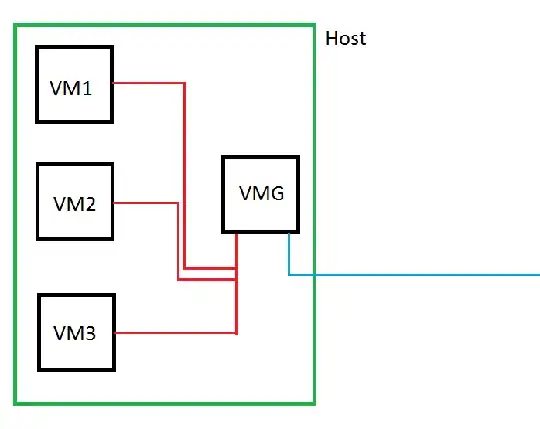
Basic information
I created a lab at home a few days ago.
I used VMware Workstation but it should work with virtualbox too:
First, I set up all VMs that belong to my lab as "host only networking" (even the gateway, but I come to this in a few words...).
You need one VM to be the gateway.
For this purpose I used a Debian 6. First I set it up as host-only-networking. The automatically added NIC will be the internal interface for your VMs that belong to the lab. Then I added an additional NIC that is bridged to my physical NIC (this will be the "external" NIC).
I configured static IPs for my gateways internal NIC and configured the lab-DHCP (runs on a Windows 2008 R2 Server) to tell his clients the internal-ip of my gateway to use it as default-gateway. My external NIC needs an IP of my LAN to communicate with my regular gateway and the internet (this external NIC needs your regular-lan-gateway-ip to be configured as default gateway since this IS your lan-gateway).
In order to get your lab-gateway working as a gateway, it's neccessary to activate routing:
echo 1 > /proc/sys/net/ipv4/ip_forward
Then you have to add your desired services like your VPN-service (my gateway runs DNS as well). You have to configure your services and iptables/firewall (basic NAT, rules to accept VPN-requests etc.).
With this environment, you can use your local network to simulate WAN. Set up a VPN-Client on your windows-host and try to connect to the "external-ip" (the regular-lan-ip) of your lab-gateway.
Edit: configure a linux-gateway
I assume, that your desired gateway-VM was installed as host-only-networking-VM and got an additional NIC bridged to your physical NIC. I used debian but it should work with ubuntu. I don't know if zeroconf disturbs manual configurations. I think ubuntu server will be more friendly to manual network configurations. If you have problems with ubuntu, try debian.
At first, you have to make sure that your gateway has a static internal IP. You configure that in /etc/network/interfaces. Here is my example-configuration:
root@lab-fw01:~# cat /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
#external interface
auto eth0
iface eth0 inet static
address 192.168.69.2
network 192.168.69.0
netmask 255.255.255.0
gateway 192.168.69.1
#internal interface
auto eth1
iface eth1 inet static
address 10.0.0.1
network 10.0.0.0
netmask 255.255.255.0
In my environment, the lab-gateway is at 10.0.0.1. That means, you have to configure the default-gateway of your clients to 10.0.0.1 (maybe via DHCP).
Internet-traffic will be forwarded to the gateway of my lab-gateways external interface (192.168.69.1), since the network-traffic is destined for an external IP-Subnet.
To get your firewall forwarding traffic for your clients, you have to enable ipv4-forwarding:
echo 1 > /proc/sys/net/ipv4/ip_forward
Your next step is to configure iptables. Because explaining how to configure iptables would oversize my answer, I'll just lead you to a good basic tutorial for iptables.
However, basic configurations for iptables may be:
- MASQUERADE all your outgoing traffic
- FORWARD ESTABLISHED and RELATED traffic to your internal network
- FORWARD outgoing traffic
- allow INPUT traffic for ssh
That's all you have to do to get the gateway running. If you're ready with this and tests are ok, you can start to install your VPN-server and configure it. Remember to add rules for VPN to iptables to allow VPN-traffic.