I had something set up wacky in our DNS setup which is now resolved.
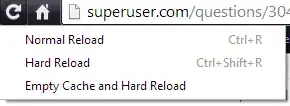
The remaining problem is that chrome has cached the incorrect setup.
Specifically, when using Chrome http://example.com is now redirecting to https://example.com (naked domain), which is not valid/supported. http://example.com SHOULD redirect to http://www.example.com and then force https://www.example.com.
But on a handful of browsers (including mine) this doesn't happen because of some funky Chrome caching. I tried going to “Privacy -> Clear Cache” but it had no effect.