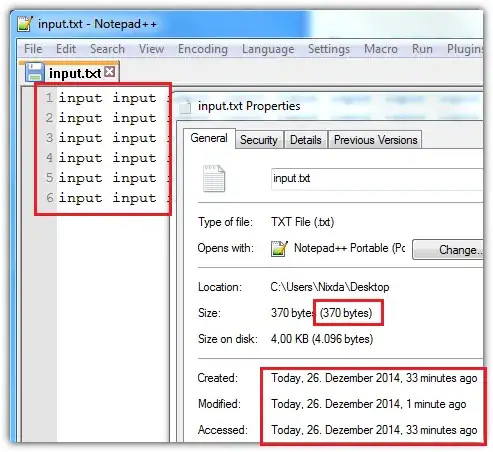
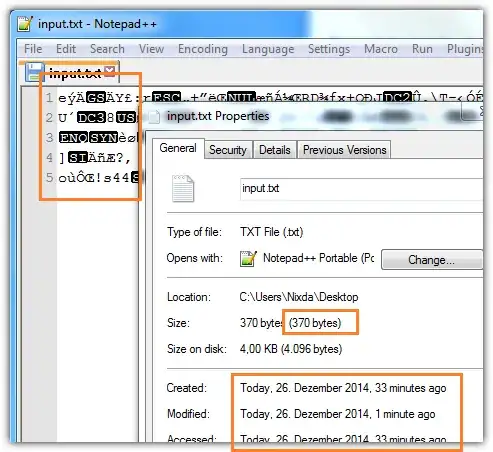
My goal is to have files of original size that can't be opened (or recovered) in their respective software such as MS Office Word. My purpose is to simulate presence of files while I don't want to share any of the files contents. Ideally file contents should be fully overwritten with random bytes while file size should stay the same as original.
I know that sometimes this can be done with hex editor or even notepad where one could change just few bytes and the file renders unusable. But it may not always work for some formats like images and audio that still could be opened but with artifacts.
For the most inquisitive of users still demanding me to answer the question "Why do you need this?" - I need this because I don't want to share my developments with some people that force me to share the files. Sometimes you just need. You can think of many other use cases - to simulate payload for file copy or backup operations, or to test the software you develop can handle junk gracefully.
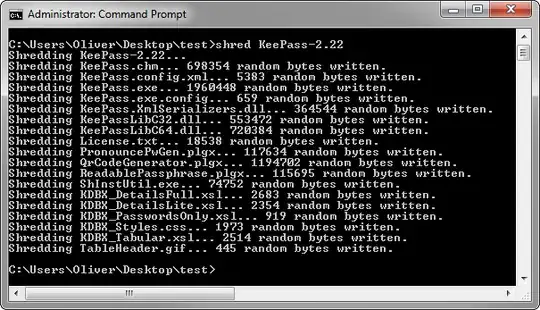
I've tested a number of secure shred utilities that are able overwrite files with random data but after that those files get deleted. I haven't seen an option to turn off the deletion step. If such an option existed that would be a solution.