I downloaded a midi file on my Windows 8.1 laptop last night. Since then, whenever I open chrome, I get a standard 'Web Page Not Available" error for ALL the sites I try to visit.
Firefox and Internet Explorer too wouldn't open ANY page. I am pretty sure that malwares are the cause as I've had similar infections before.
I ran scans using the following tools in both safe mode and normal mode(using latest signatures)
1) Malwarebytes Antimalware
2) Spybot
3) Microsoft Anti-Malware tool
I even ran a McAfee scan for virus.
Surprisingly all malware removal tools and McAfee failed to detect even a single object!
I was quite surprised because last time , I resolved the issue by using the malware removal tools (which detected objects and deleted them).
However, after spending hours on google, I found out the issue can be resolved running the ipconfig /flushdns command in cmd. I tried it and the issue was resolved TEMPORARILY. But if I close and restart chrome or if I leave chrome idle for some time , the issue reappears again.
I have tried resetting winsock and ip using the following cmd commands with no respite -
netsh winsock reset
netsh winsock reset catalog
netsh int ipv4 reset reset.log
netsh int ipv6 reset reset.log
netsh int ip reset c:\resetlog.txt
I even ran the Avira DNS Repair Tool . But it said there was no need for repairing as the DNS settings were not altered by DNS Changing malware.
I would appreciate a good solution ASAP as I'm not able to use the internet.
Note -
1) I connect to the modem using wifi. I tried connecting using LAN wire later but it made no difference.
2) There are NO connectivity issues while connecting via both modes.
Thanks in advance!
EDIT
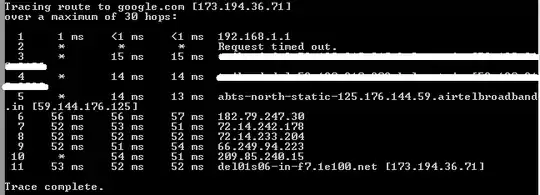
This is my trace route to google.com