I am trying to prevent users from accidentally deleting a certain folder in a parent folder, while still giving them modify permission on all other files and folders in the parent folder. But they should be also able to modify files and folders in this certain folder.
On this comment to a similar problem my problem is described very good, but there was no answer to this comment. https://superuser.com/a/977180/554054 This is my structur:
Folder A
|-Folder B
|-Folder C
| |+Folder E
| | |+ a.doc
| |+Folder F
| | |+ b.doc
| |+c.doc
|-D
- Folder A - Read/Execute
- Folder B/D - Read/Execute (inherited from A) + Read/Write/Delete for Fils/Subfolders
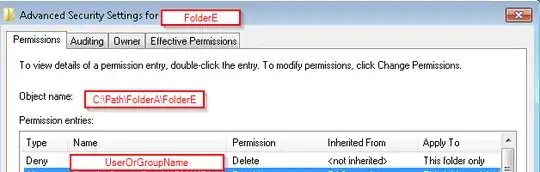
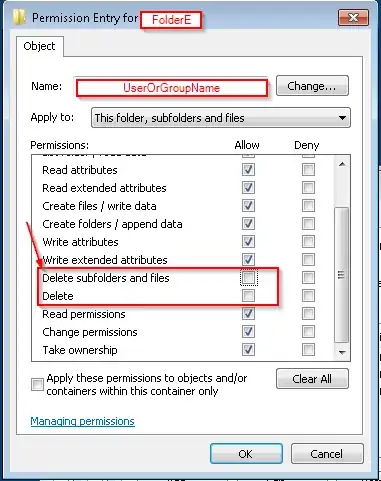
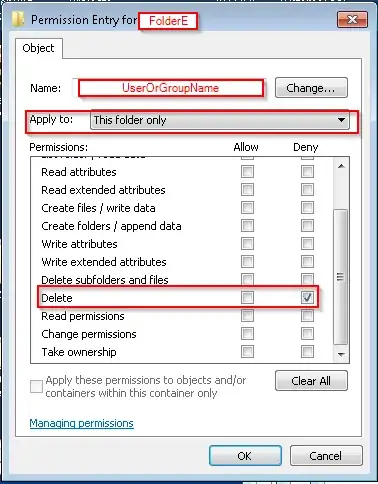
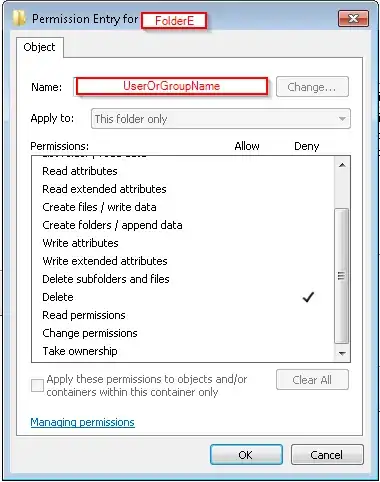
- Folder C - Read/Execute (inherited from A) + Read/Write/Delete for Fils/Subfolders, EXCEPT for Folder E! This Folder shouldn´t be allowed to delete, but in the Folder the user should be able to read/write/delete subfolders and files.
i tried many different ways of permission combinations, but nothing worked. Has anyone an idea how to solve this problem?
Here are two screenshots of my Advanced Settings for the Folder E: Advanced Settings Folder E inherited special Permissions for the User "Bearbeiter"