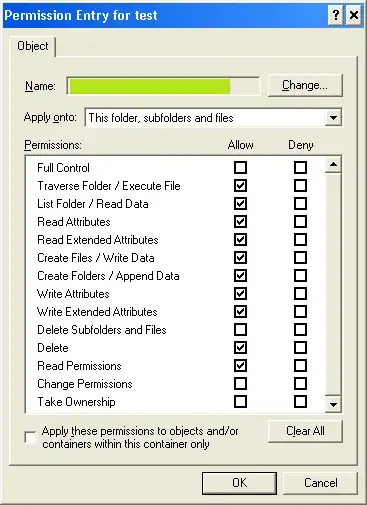
As Graham pointed out, using multiple permissions entries for the same user (something I had never tried before) was the key here:

The permissions on the parent folder give the users almost absolute freedom to make any change... except that the "delete" box is unchecked - so users cannot delete/move/rename this important folder by accident:
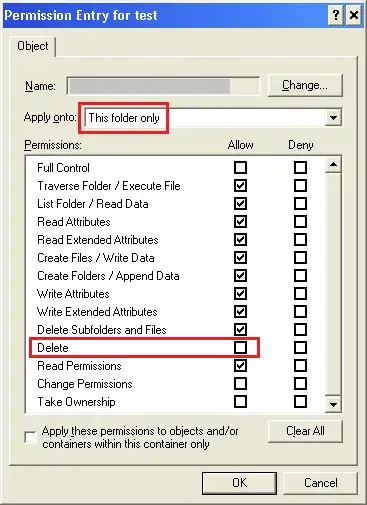
Moving on to the second permission set for the same user (which apply not to the folder itself, but to its contents), we see the exact same rights granted to the user, including "delete" privileges.
So, users can do anything they wish to the subfolders and files, including deleting/moving/renaming them.
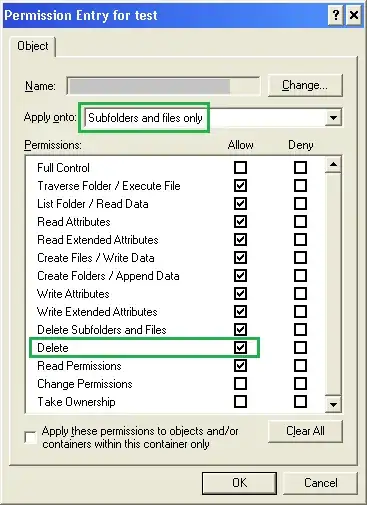
This configuration allows me to protect key folders, such as personalised target scan directories which reside in user personal network locations. Users can modify the contents (such as deleting PDFs of scans they no longer wish to keep), but cannot inadvertently cause problems for themselves by deleting a folder the scanner expects to see when saving to the network.
I had to disable inheritance for the special folder as it was otherwise not possible to make changes to the user's permissions which varied from the root of the network share; however, all subfolders and objects do use inheritance in order to obtain their permissions from their parent folder.
Once I figured out exactly what needed to be done, this only took a couple of minutes to adjust for each user. I now have peace of mind that key network folders cannot accidentally get deleted by users.