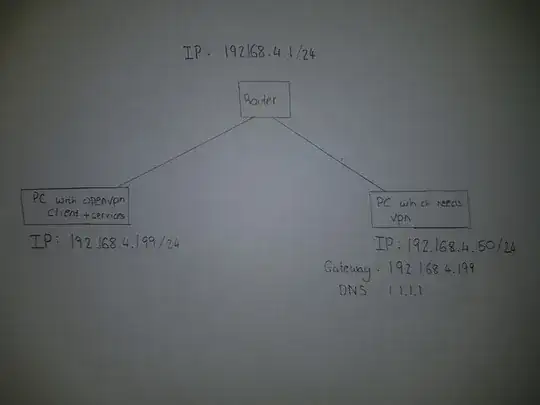
I am trying to share a vpn clients with other nodes on the lan. I have an ubuntu server running a openvpn client on my LAN. The following is my network diagram:
The server is also running some web services which need to be accessible on WAN - when I turn the VPN on, this setup works, but the services are no longer accessible. As per this question, I added the following to my openvpn config:
route-nopull
route 192.168.4.50 255.255.255.255
When I run ip route list:
default via 192.168.4.1 dev enp1s0 proto static metric 100
10.175.0.69 dev tun0 proto kernel scope link src 10.175.0.70
169.254.0.0/16 dev enp1s0 scope link metric 1000
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 linkdown
172.18.0.0/16 dev br-616f4053c28b proto kernel scope link src 172.18.0.1
192.168.4.0/24 dev enp1s0 proto kernel scope link src 192.168.4.199 metric 100
192.168.4.50 via 10.175.0.69 dev tun0
With route-nopull, the node has internet access, but not through the VPN
full openvpn config (without the keys):
dev tun
fast-io
persist-key
persist-tun
nobind
remote XXXXXXX 1195
#script-security 2
#up /etc/openvpn/up.sh
remote-random
pull
comp-lzo no
tls-client
verify-x509-name Server name-prefix
ns-cert-type server
key-direction 1
route-method exe
route-delay 2
tun-mtu 1500
fragment 1300
mssfix 1200
verb 3
cipher AES-256-CBC
keysize 256
auth SHA512
sndbuf 524288
rcvbuf 524288
auth-user-pass /etc/openvpn/login
route-nopull
route 192.168.4.50 255.255.255.255
UPDATE: This script is run when the VPN is enabled. In the last 2 lines, I am attempting to allow data on specific ports to bypass the vpn - but this breaks it.
#!/bin/sh
INTIF=enp1s0 # internal interface (your LAN)
EXTIF=tun0 # external interface (WAN via OpenVPN)
#iptables -t nat -A POSTROUTING -o $EXTIF -j MASQUERADE
iptables -A FORWARD -i $EXTIF -o $INTIF -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FORWARD -i $INTIF -o $EXTIF -j ACCEPT
iptables -A FORWARD -i $EXTIF -o $EXTIF -p tcp --sport 7878 --dport 7878 -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FORWARD -i $EXTIF -o $EXTIF -p tcp --sport 7878 --dport 7878 -j ACCEPT