I'm trying to delete an executable, but it fails with the error Access is denied even adding /F to force it as del /F system.exe. I'm using an elevated Command Prompt.
Attempting to delete the file through Windows Explorer yields the following:
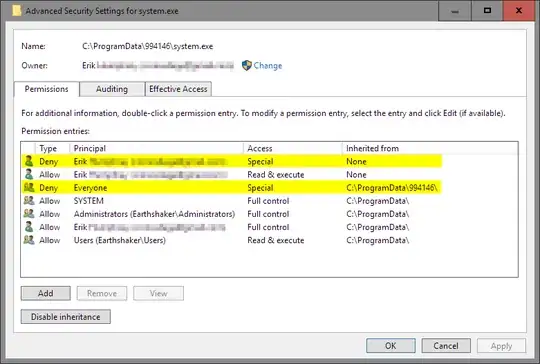
I went into the Security properties of the executable. Highlighted are the odd permission entries which may be stopping me from deleting this file:
Originally, it did not let me delete the entries; the option was greyed out. I performed takeown /F C:\ProgramData\994146\system.exe, deleted the entries, added ones which gave me full permissions, and closed the dialogue box. The error persisted. When I reopened the Advanced Security Settings, the entries were back.
The parent folder of system.exe, 994146, is completely invisible in ProgramData. I have "show hidden files" on ProgramData. I had to manually type the path in Windows Explorer's address bar. I am also not sure how to edit the properties of 994146 since I can not select it in the file hierarchy.