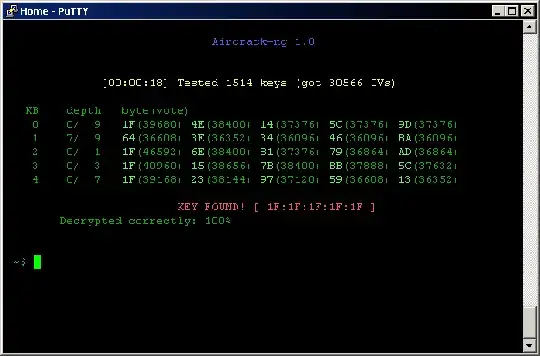
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK keys cracking program that can recover keys once enough data packets have been captured. It can be used for auditing wireless networks.
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK keys cracking program that can recover keys once enough data packets have been captured. It can be used for auditing 802.11a, 802.11b and 802.11g wireless networks.
The software runs on Windows and Linux.