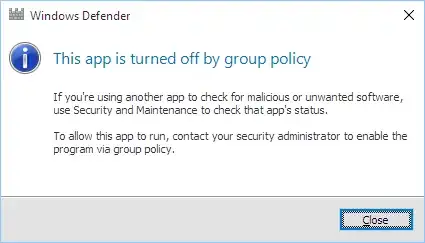
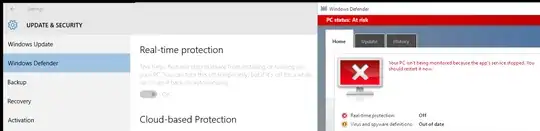
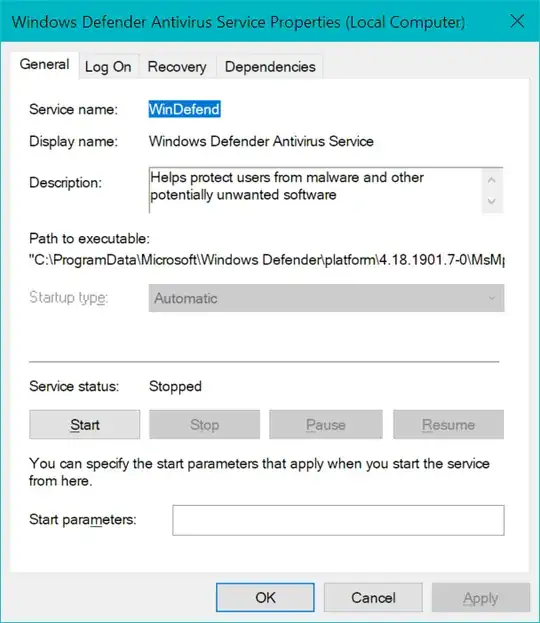
I have written the batch file and registry files that should completely disable Windows Defender in Windows 10.
- Save the following files into the same folder.
- Run
Disable Windows Defender.bat as administrator.
- After the batch file is done, restart.
- The latest versions of Windows 10 make it difficult to terminate the "MsMpEng.exe" process, so you will have to boot into a different operating system and rename or delete the Windows Defender folders in Program Files manually before proceeding to the next step.
- Run
Disable Windows Defender.bat again as administrator.
- Windows Defender should be completely disabled now.
Disable Windows Defender.bat
@echo off
call :main %*
goto :eof
:main
setlocal EnableDelayedExpansion
rem Check if Windows Defender is running.
tasklist /fi "imageName eq "MsMpEng.exe"" | find /i "MsMpEng.exe" > nul 2> nul
if %errorLevel% equ 0 (
rem Windows Defender is running.
echo Windows Defender is running.
rem Performable operations while Windows Defender is running.
rem Disable Windows Defender drivers.
echo Disabling Windows Defender drivers...
set "drivers="%SystemRoot%\System32\drivers\WdBoot.sys";"%SystemRoot%\System32\drivers\WdFilter.sys";"%SystemRoot%\System32\drivers\WdNisDrv.sys""
set "drivers=!drivers:""="!"
set "wasDriverDisabled=false"
for %%d in (!drivers!) do (
if exist "%%~d" (
echo Disabling Windows Defender driver "%%~d"...
call :disableFile "%%~d"
set "wasDriverDisabled=true"
)
)
rem Disable Windows Defender objects.
echo Disabling Windows Defender objects...
call :importRegistry "Disable Windows Defender objects.reg"
rem Require restart to unload Windows Defender drivers and objects.
echo.
echo Restart required.
) else (
rem Windows Defender is not running.
echo Windows Defender is not running.
rem Performable operations while Windows Defender is not running.
rem Disable Windows Defender features.
echo Disabling Windows Defender features...
call :importRegistry "Disable Windows Defender features.reg"
rem Disable Windows Defender services.
echo Disabling Windows Defender services...
call :importRegistry "Disable Windows Defender services.reg"
rem Disable Windows Defender files.
echo Disabling Windows Defender files...
ren "%ProgramFiles%\Windows Defender" "Windows Defender.bak"
ren "%ProgramFiles(x86)%\Windows Defender" "Windows Defender.bak"
ren "%ProgramData%\Microsoft\Windows Defender" "Windows Defender.bak"
)
endlocal
goto :eof
:ownFile
setlocal
set "filePath=%~1"
set "user=%~2"
takeown /f "%filePath%" /a
icacls "%filePath%" /grant "%user%:F"
endlocal
goto :eof
:disableFile
setlocal
set "filePath=%~1"
call :ownFile "%filePath%" "Administrators"
ren "%filePath%" "%~nx1.bak"
endlocal
goto :eof
:importRegistry
setlocal
set "filePath=%~1"
call OwnRegistryKeys.bat "%filePath%"
@echo off
regedit /s "%filePath%"
endlocal
goto :eof
Disable Windows Defender objects.reg
Windows Registry Editor Version 5.00
; Disable "Scan with Windows Defender..." right click context menu.
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{09A47860-11B0-4DA5-AFA5-26D86198A780}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{09A47860-11B0-4DA5-AFA5-26D86198A780}]
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{D8559EB9-20C0-410E-BEDA-7ED416AECC2A}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{D8559EB9-20C0-410E-BEDA-7ED416AECC2A}]
; Disable PSFactoryBuffer ("mpuxhostproxy.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{13F6A0B6-57AF-4BA7-ACAA-614BC89CA9D8}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{13F6A0B6-57AF-4BA7-ACAA-614BC89CA9D8}]
; Disable "DefenderCSP.dll".
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{195B4D07-3DE2-4744-BBF2-D90121AE785B}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{195B4D07-3DE2-4744-BBF2-D90121AE785B}]
; Disable Windows Defender IOfficeAntiVirus implementation ("MpOav.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{2781761E-28E0-4109-99FE-B9D127C57AFE}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{2781761E-28E0-4109-99FE-B9D127C57AFE}]
; Disable InfectionState WMI Provider ("MpProvider.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{361290c0-cb1b-49ae-9f3e-ba1cbe5dab35}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{361290c0-cb1b-49ae-9f3e-ba1cbe5dab35}]
; Disable Status WMI Provider ("MpProvider.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{8a696d12-576b-422e-9712-01b9dd84b446}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{8a696d12-576b-422e-9712-01b9dd84b446}]
; Disable PSFactoryBuffer ("mpuxhostproxy.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{94F35585-C5D7-4D95-BA71-A745AE76E2E2}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{94F35585-C5D7-4D95-BA71-A745AE76E2E2}]
; Disable Microsoft Windows Defender ("MsMpCom.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{A2D75874-6750-4931-94C1-C99D3BC9D0C7}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{A2D75874-6750-4931-94C1-C99D3BC9D0C7}]
[-HKEY_LOCAL_MACHINE\Software\Classes\TypeLib{8C389764-F036-48F2-9AE2-88C260DCF43B}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\TypeLib{8C389764-F036-48F2-9AE2-88C260DCF43B}]
; Disable Windows Defender WMI Provider ("ProtectionManagement.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{A7C452EF-8E9F-42EB-9F2B-245613CA0DC9}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{A7C452EF-8E9F-42EB-9F2B-245613CA0DC9}]
; Disable AMMonitoring WMI Provider ("AMMonitoringProvider.dll").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{DACA056E-216A-4FD1-84A6-C306A017ECEC}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{DACA056E-216A-4FD1-84A6-C306A017ECEC}]
; Disable MP UX Host ("MpUxSrv.exe").
[-HKEY_LOCAL_MACHINE\Software\Classes\CLSID{FDA74D11-C4A6-4577-9F73-D7CA8586E10D}]
[-HKEY_LOCAL_MACHINE\Software\Classes\Wow6432Node\CLSID{FDA74D11-C4A6-4577-9F73-D7CA8586E10D}]
Disable Windows Defender features.reg
Windows Registry Editor Version 5.00
; Disable Windows Defender features.
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows Defender]
"DisableAntiSpyware"=dword:00000001
"DisableRoutinelyTakingAction"=dword:00000001
"ProductStatus"=dword:00000000
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows Defender\Real-Time Protection]
"DisableAntiSpywareRealtimeProtection"=dword:00000001
"DisableRealtimeMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows Defender\Scan]
"AutomaticallyCleanAfterScan"=dword:00000000
"ScheduleDay"=dword:00000008
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows Defender\UX Configuration]
"AllowNonAdminFunctionality"=dword:00000000
"DisablePrivacyMode"=dword:00000001
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows Defender]
"DisableAntiSpyware"=dword:00000001
"DisableRoutinelyTakingAction"=dword:00000001
"ProductStatus"=dword:00000000
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows Defender\Real-Time Protection]
"DisableAntiSpywareRealtimeProtection"=dword:00000001
"DisableRealtimeMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows Defender\Scan]
"AutomaticallyCleanAfterScan"=dword:00000000
"ScheduleDay"=dword:00000008
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows Defender\UX Configuration]
"AllowNonAdminFunctionality"=dword:00000000
"DisablePrivacyMode"=dword:00000001
Disable Windows Defender services.reg
Windows Registry Editor Version 5.00
; Disable "Windows Defender" services.
[HKEY_LOCAL_MACHINE\System\ControlSet001\Services\WinDefend]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\WinDefend]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WinDefend]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet001\Services\WdBoot]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\WdBoot]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WdBoot]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet001\Services\WdFilter]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\WdFilter]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WdFilter]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet001\Services\WdNisDrv]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\WdNisDrv]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WdNisDrv]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet001\Services\WdNisSvc]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\WdNisSvc]
"Start"=dword:00000004
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WdNisSvc]
"Start"=dword:00000004
OwnRegistryKeys.bat
@echo off
rem Get the location of the PowerShell file.
for /f "usebackq tokens=" %%f in (where "OwnRegistryKeys.ps1") do (
rem Run command for each argument.
for %%a in (%) do (
powershell -executionPolicy bypass -file "%%~f" "%%~a"
)
)
OwnRegistryKeys.ps1
$script:baseKey = @{
"HKEY_CLASSES_ROOT" = @{
"name" = "HKEY_CLASSES_ROOT";
"shortName" = "HKCR";
"key" = [Microsoft.Win32.Registry]::ClassesRoot
};
"HKEY_CURRENT_CONFIG" = @{
"name" = "HKEY_CURRENT_CONFIG";
"shortName" = "HKCC";
"key" = [Microsoft.Win32.Registry]::CurrentConfig
};
"HKEY_CURRENT_USER" = @{
"name" = "HKEY_CURRENT_USER";
"shortName" = "HKCU";
"key" = [Microsoft.Win32.Registry]::CurrentUser
};
"HKEY_DYN_DATA" = @{
"name" = "HKEY_DYN_DATA";
"shortName" = "HKDD";
"key" = [Microsoft.Win32.Registry]::DynData
};
"HKEY_LOCAL_MACHINE" = @{
"name" = "HKEY_LOCAL_MACHINE";
"shortName" = "HKLM";
"key" = [Microsoft.Win32.Registry]::LocalMachine
};
"HKEY_PERFORMANCE_DATA" = @{
"name" = "HKEY_PERFORMANCE_DATA";
"shortName" = "HKPD";
"key" = [Microsoft.Win32.Registry]::PerformanceData
};
"HKEY_USERS" = @{
"name" = "HKEY_USERS";
"shortName" = "HKU";
"key" = [Microsoft.Win32.Registry]::Users
}
}
function enablePrivilege {
param(
# The privilege to adjust. This set is taken from:
# http://msdn.microsoft.com/en-us/library/bb530716(VS.85).aspx
[validateSet(
"SeAssignPrimaryTokenPrivilege",
"SeAuditPrivilege",
"SeBackupPrivilege",
"SeChangeNotifyPrivilege",
"SeCreateGlobalPrivilege",
"SeCreatePagefilePrivilege",
"SeCreatePermanentPrivilege",
"SeCreateSymbolicLinkPrivilege",
"SeCreateTokenPrivilege",
"SeDebugPrivilege",
"SeEnableDelegationPrivilege",
"SeImpersonatePrivilege",
"SeIncreaseBasePriorityPrivilege",
"SeIncreaseQuotaPrivilege",
"SeIncreaseWorkingSetPrivilege",
"SeLoadDriverPrivilege",
"SeLockMemoryPrivilege",
"SeMachineAccountPrivilege",
"SeManageVolumePrivilege",
"SeProfileSingleProcessPrivilege",
"SeRelabelPrivilege",
"SeRemoteShutdownPrivilege",
"SeRestorePrivilege",
"SeSecurityPrivilege",
"SeShutdownPrivilege",
"SeSyncAgentPrivilege",
"SeSystemEnvironmentPrivilege",
"SeSystemProfilePrivilege",
"SeSystemtimePrivilege",
"SeTakeOwnershipPrivilege",
"SeTcbPrivilege",
"SeTimeZonePrivilege",
"SeTrustedCredManAccessPrivilege",
"SeUndockPrivilege",
"SeUnsolicitedInputPrivilege"
)]
$privilege,
# The process on which to adjust the privilege. Defaults to the current process.
$processId = $pid,
# Switch to disable the privilege, rather than enable it.
[switch] $disable
)
# Taken from P/Invoke.NET with minor adjustments.
$definition = @'
using System;
using System.Runtime.InteropServices;
public class AdjustPrivilege {
[DllImport("advapi32.dll", ExactSpelling = true, SetLastError = true)]
internal static extern bool AdjustTokenPrivileges(IntPtr htok, bool disall, ref TokPriv1Luid newst, int len, IntPtr prev, IntPtr relen);
[DllImport("advapi32.dll", ExactSpelling = true, SetLastError = true)]
internal static extern bool OpenProcessToken(IntPtr h, int acc, ref IntPtr phtok);
[DllImport("advapi32.dll", SetLastError = true)]
internal static extern bool LookupPrivilegeValue(string host, string name, ref long pluid);
[StructLayout(LayoutKind.Sequential, Pack = 1)]
internal struct TokPriv1Luid {
public int Count;
public long Luid;
public int Attr;
}
internal const int SE_PRIVILEGE_ENABLED = 0x00000002;
internal const int SE_PRIVILEGE_DISABLED = 0x00000000;
internal const int TOKEN_QUERY = 0x00000008;
internal const int TOKEN_ADJUST_PRIVILEGES = 0x00000020;
public static bool EnablePrivilege(long processHandle, string privilege, bool disable) {
bool result;
TokPriv1Luid tp;
IntPtr hproc = new IntPtr(processHandle);
IntPtr htok = IntPtr.Zero;
result = OpenProcessToken(hproc, TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, ref htok);
tp.Count = 1;
tp.Luid = 0;
if (disable) {
tp.Attr = SE_PRIVILEGE_DISABLED;
} else {
tp.Attr = SE_PRIVILEGE_ENABLED;
}
result = LookupPrivilegeValue(null, privilege, ref tp.Luid);
result = AdjustTokenPrivileges(htok, false, ref tp, 0, IntPtr.Zero, IntPtr.Zero);
return result;
}
}
'@
$processHandle = (get-process -id $processId).handle
$type = add-type $definition -passThru
$type[0]::EnablePrivilege($processHandle, $privilege, $disable)
}
function getKeyNames {
param(
[parameter(mandatory = $true)]
[string[]] $filePaths = $null
)
return (get-content $filePaths | select-string -pattern "\[\-?(.*)\]" -allMatches | forEach-object {$_.matches.groups[1].value} | get-unique)
}
function splitKeyName {
param(
[parameter(mandatory = $true)]
[string] $keyName = $null
)
$names = $keyName.split("\\/", 2)
$rootKeyName = $names[0]
$subKeyName = $names[1]
$keyPart = @{
root = $baseKey[$rootKeyName];
subKey = @{
name = $subKeyName
}
}
return $keyPart
}
function ownRegistryKey {
param(
[parameter(mandatory = $true)]
[string] $keyName = $null
)
write-host """$keyName"""
# Check if the key exists.
if ($(try { test-path -path "Registry::$keyName".trim() } catch { $false })) {
write-host " Opening..."
$keyPart = splitKeyName -keyName $keyName
$ownableKey = $keyPart.root.key.openSubKey($keyPart.subKey.name, [Microsoft.Win32.RegistryKeyPermissionCheck]::ReadWriteSubTree, [System.Security.AccessControl.RegistryRights]::TakeOwnership)
if ($ownableKey -ne $null) {
# Set the owner.
write-host " Setting owner..."
$acl = $ownableKey.getAccessControl([System.Security.AccessControl.AccessControlSections]::None)
$owner = [System.Security.Principal.NTAccount] "Administrators"
$acl.setOwner($owner)
$ownableKey.setAccessControl($acl)
# Set the permissions.
write-host " Setting permissions..."
$acl = $ownableKey.getAccessControl()
$person = [System.Security.Principal.NTAccount] "Administrators"
$access = [System.Security.AccessControl.RegistryRights] "FullControl"
$inheritance = [System.Security.AccessControl.InheritanceFlags] "ContainerInherit"
$propagation = [System.Security.AccessControl.PropagationFlags] "None"
$type = [System.Security.AccessControl.AccessControlType] "Allow"
$rule = new-object System.Security.AccessControl.RegistryAccessRule($person, $access, $inheritance, $propagation, $type)
$acl.setAccessRule($rule)
$ownableKey.setAccessControl($acl)
$ownableKey.close()
write-host " Done."
# Own children subkeys.
$readableKey = $keyPart.root.key.openSubKey($keyPart.subKey.name, [Microsoft.Win32.RegistryKeyPermissionCheck]::ReadSubTree, [System.Security.AccessControl.RegistryRights]::ReadKey)
if ($readableKey -ne $null) {
$subKeyNames = ($readableKey.getSubKeyNames() | forEach-object { "$keyName\$_" })
$readableKey.close()
if ($subKeyNames -ne $null) {
ownRegistryKeys -keyNames $subKeyNames
}
} else {
write-host " Unable to open children subkeys."
}
} else {
write-host " Unable to open subkey."
}
} else {
write-host " Key does not exist."
}
write-host
}
function ownRegistryKeys {
param(
[parameter(mandatory = $true)]
[string[]] $keyNames = $null
)
$keyName = $null
foreach ($keyName in $keyNames) {
# Own parent key and children subkeys.
ownRegistryKey -keyName $keyName
}
}
function requestPrivileges {
$numberOfRetries = 10
$privilegeResult = $false
for ($r = 0; !$privilegeResult -band $r -lt $numberOfRetries; $r += 1) {
$privilegeResult = enablePrivilege -privilege "SeTakeOwnershipPrivilege"
}
if (!$privilegeResult) {
write-host "Unable to receive privilege."
exit 1
}
}
function main {
param(
[parameter(mandatory = $true)]
[string[]] $filePaths = $null
)
requestPrivileges
$keyNames = getKeyNames -filePaths $filePaths
ownRegistryKeys -keyNames $keyNames
}
main $args